Chief Marketing Officer
In the world of cybersecurity threat detection and response, EDR (endpoint detection and response) is often touted as the most important element of a business’ security strategy. EDR, as its name implies, focuses on endpoint protection—meaning all the devices that connect to the business network. So, there’s a good reason for the emphasis especially given the distributed environments we all operate in today. Access to the endpoint gives adversaries access to the network.
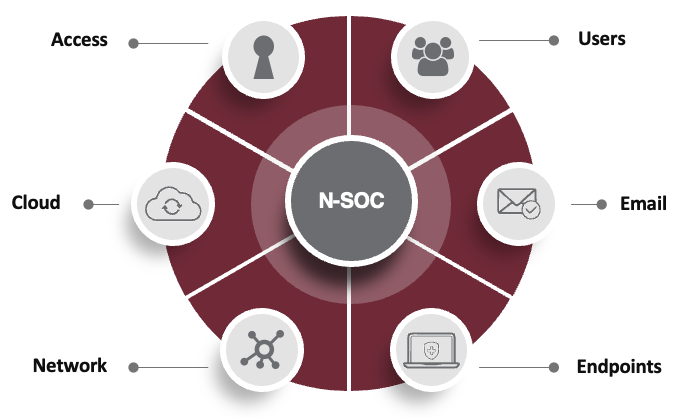
XDR includes EDR and goes beyond it—to provide protection across common threat vectors in your tech stack like the network, endpoints, email, firewall, cloud, and more. The concept behind the “X” in XDR is to close security gaps across any and all threat vectors. This includes the endpoint and also other key areas of vulnerability such as network, cloud, etc.
Think of XDR as you would defending a castle. There are layers of security built in to keep specific threats out, like the moat around the castle and high walls. Built into XDR’s layered defense are specific response tactics fine-tuned for each type of attack. These tactics are your archers, swordsmen, and hand-to-hand combatants. The goal is to take out as many attackers as you can to diminish or neutralize the attack before it reaches the castle walls. Those who do reach the castle wall are met with stronger force. XDR defends your corporate “castle” across the many different elements of cybersecurity, providing a much broader scope.
For advanced cybersecurity protection, XDR has already replaced EDR as the only way to provide real protection from the digital threats a company faces. Endpoint protection is an important piece of an overall security strategy, but EDR on its own leaves a business woefully unprotected from existing and future threats. In this article, we’ll offer more detail for questions like:
- What is the difference between XDR and EDR?
- How do MDR, SIEM, antivirus, and firewalls fit into this equation?
- What does XDR offer that EDR lacks?
What Is the Difference Between EDR and XDR?
EDR is a component of cybersecurity that collects data from endpoints, then monitors and analyzes this data to detect and respond to cyberattacks. Its main capabilities include:
- Gathering telemetry from endpoints that connect to the company network, like computers, mobile phones, servers, and IoT (Internet of Things) devices
- Analyzing gathered data to detect threats and threat patterns
- Notifying business IT team or contracted security providers
- Removing or containing threats that do make it into the network
XDR stands for extended detection and response, and its purpose is to find and remove security threats from any vector — not just the endpoints. While endpoints are high value targets for cybercriminals, it’s not the only way they get in nor the only way they do damage.
Common threat vectors:
XDR monitors and protects the entire range of a business’ systems, including:
- Cloud access security broker (CASB)
- Cloud workload protection platform (CWPP)
- Containers
- Email (beyond gateway-based protection)
- Firewall
- Identity
- Internet of Things (IoT)
- Operational technology (OT)
- Network
- Web
- Zero trust architecture (ZTA)
With this broad perspective, XDR gives cybersecurity teams a comprehensive view of a company’s security posture and vulnerabilities. XDR stations more guards around your digital assets to discover, stop, and prevent cybercrime.
How Do Other Cybersecurity Measures Fit into the XDR Framework?
There are several other terms that are frequently used alongside EDR and XDR. Understanding the difference between these terms and how they relate to comprehensive business security helps better understand XDR and EDR more thoroughly. Let’s look at four of the most common in more detail.
EDR vs MDR vs XDR
Managed detection and response (MDR) is a cybersecurity service delivered by a managed security provider, like DataEndure, that manages all or part of a company’s cybersecurity. MDR combines technology and human expertise to perform threat hunting, monitoring, and response across endpoints as well as the network (whereas EDR is endpoint specific).
The main benefit of MDR is that it helps companies rapidly identify and limit the impact of a broader scope of threats without the need for additional (internal) staffing. Two important things to note:
- Some MDR services require you to “bring your own technology”, in other cases it’s included as part of your service. Make sure you know the difference.
- Some offer a 24x7x365 Security Operations Center (SOC), but many don’t. A SOC is a critical element to a full MDR solution.
XDR delivers on its name. It offers the most comprehensive threat detection and response capabilities, covering all threat vectors to protect you on all fronts. Make sure you inspect any solution you consider—there are a lot of vendors calling their capabilities “extended” when really tacking limited features on but they’re not integrated nor comprehensive.
Antivirus vs EDR vs XDR
Antivirus protection has been around since before computers could connect to the internet. Its roots go back to scanning signatures, meaning it compares incoming code to known malicious code and blocks harmful files from entering. EDR provides this and so much more. The threats to the endpoint have evolved, and so has the security solution.
Today’s endpoint defense (EDR) requires a layered solution with advanced threat detection, investigation, and response capabilities. With incident data search and investigation alert triage, suspicious activity validation, threat hunting, and malicious activity detection and containment, you accelerate threat detection, response, and remediation.
The next evolution in security, XDR, represents a transformational shift in how organizations defend and protect their digital assets. Instead of a tool for this and a tool for that, XDR offers a comprehensive coverage across all threat vectors. XDR protects all threat vectors, not just the endpoints. XDR and EDR solutions will likely include antivirus capabilities as part of their broader solutions.
Without expert human intelligence, any EDR, MDR, or XDR tool will inevitably fail to protect you. Foundational to any of these solutions is human eyes on glass. You need a dedicated 24×7 security operations center (SOC) trained to pick up on patterns and correlate data to thwart nefarious actors.
Firewall vs EDR
A firewall filters traffic into and out of a network. It is a reactive form of protection that prevents access to the network for unauthorized users. EDR and XDR solutions usually include a firewall as part of the overall defenses, but they also include proactive defenses.
However, as employees and data have become distributed, there’s no definitive network edge, which limits the efficacy of a firewall. This is a gap that adversaries know about and exploit, so make sure your solution takes this into account.
Why Is XDR Better than EDR?
XDR is better than EDR because it covers all threat vectors, not just the endpoint. Endpoints are only one entry point for adversaries; with EDR alone you leave every other weakness exposed. In fact, of the 76% of organizations targeted each year, 64% of them are infected and only half are ever able to retrieve their lost data and recover fully. XDR protection helps keep you from becoming a statistic (or a headline).
What Is the Downside of EDR?
EDR lacks advanced monitoring and protection for five out of six threat vectors. XDR offers security across all vectors, meaning your business is fully protected in a way that EDR alone cannot achieve.
DataEndure: XDR Solutions, Simplified
With so many XDR tools to choose from, getting it right can feel daunting and take up a lot of time. That’s where DataEndure comes in. Strong cybersecurity is a mindset, not just a set of tools. We understand you’ve likely made security investments, so we’ll assess what you’ve got and help you close critical gaps quickly. Because every minute counts when an adversary is in your environment.
At DataEndure, we…
- Cut nefarious dwell time to minutes, not months.
- Are vendor- and tool-agnostic, so you can keep what already works for you
- Help you meet compliance regulations in your industry
- Accelerate your security maturity within 30-90 days (we guarantee it)
- Reduce your cost by 50% vs building on your own
Contact us today to accelerate your security maturity. Not sure where your vulnerabilities are? We can help–our complimentary security health check reveals where you might be at risk.