Chief Marketing Officer
Security solutions such as threat detection and response (TDR) or endpoint detection and response (EDR) have become the “go-to” for companies looking to better protect their data and prevent cyberattacks within their systems. Despite an average cybersecurity budget increase of 29% in 2023, cyber experts say they need a further 40% rise to be confident in their ability to mitigate security risks.
While cybersecurity can be costly, the cost of recovering from a breach can be much greater. The greatest variable to your cost depends on whether you’re buying it or consuming through a managed security service provider (MSSP).
Here are some cost considerations as you evaluate an EDR solution:
- Pricing can vary greatly from vendor to vendor.
- Solutions are often priced by the number of endpoints being monitored.
- Some EDR licenses include cloud hosting, others do not.
Like other IT investments, purchase price is solely one factor. To get the full value out of EDR, consider the following:
- Do you have appropriate in-house staff? (threat researchers, threat hunters, data scientists to fine-tune detection models, incident responders, application developers for integration and automation, and IT operations personnel).
- Are you equipped to do this 24x7x365?
- Do you have a function dedicated to stay on top of emerging threats and waning tool efficacy to maintain your security controls?
EDR requires an in-house investment. You either need to bring in people, tools, and process or you consume the solution through a managed security service provider (MSSP). Typically outsourcing will reduce your costs by 50%, you’ll get broader access to expertise, 24x7x365 always on, better cost efficiency, everything you need without delays.
If you go with an MSSP, be sure to inspect what you think is included as part of the service. There can be hidden fees, so here are main questions you should ask:
- Do they charge extra for faster response times?
- Is telemetry correlation included?
- Do they charge for ingested data–or processed data?
- Do you buy the tools–or do they?
- Do they have a 24/7/365 security operations team (SOC)?
- Is the SOC included as part of the service?
What Is EDR?
Work from anywhere means your people, devices, and data are everywhere. Because cybercriminals target the endpoint, there’s pressing urgency for Endpoint detection and response (EDR) solutions. EDR continuously monitors endpoints. In theory, endpoint detection and response tools deliver real-time detection and remediation of complex threats with no need for human intervention. It also delivers advanced analytics for clarity on the condition of each and every endpoint in real time.
What Information Does EDR Collect?
EDR collects information and data through any and all endpoints within a company. These endpoints could include laptops, mobile devices, IoT, servers, etc.—anything that accesses the network.
EDR looks for suspicious behavior that may be an indication of compromise. For example, it looks at what’s happening on the endpoint: who has logged in on a machine, what programs are run, and the names of files that are read or written. It also analyzes internet connections for anomalous behavior.
EDR vs XDR
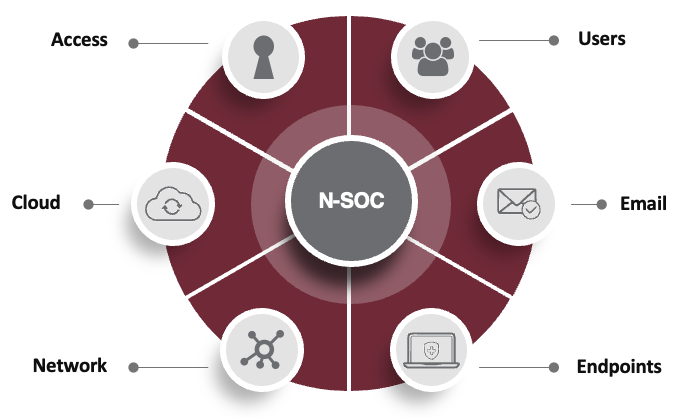
EDR solely defends the endpoint. Extended detection and response (XDR) provides a layered approach–defending across all threat vectors (endpoint, network, email, user, cloud, access) for the strongest security posture. XDR solutions enhance visibility and extend the capability to promptly detect and respond to identified threats and malicious activities. A true XDR solution should include a security operations center (SOC) of cybersecurity experts who evaluate and analyze alerts and data that XDR tools gather to identify and neutralize security threats.
So, what makes XDR different from EDR? According to Forrester, XDR is the evolution of EDR, providing better cybersecurity for businesses. Let’s break down some of the key differences between the two.
To start, EDR software:
- Monitors only endpoints and records indicators of malicious activity
- Detects and sends out alerts of any suspicious activity
- Validates potentially harmful activity
- Analyzes data
- Provides forensic information after detecting and responding to threats
On the other hand, an XDR solution:
- Accelerates security maturity (30-90 days) across all threat vectors
- Consolidates cybersecurity tools
- Lowers operational costs
- Increases efficiency
- Delivers on-demand 24×7 expertise
- Escalates only the alerts that require attention
- Proactive threat hunting
- Continuous Incident Response (CIR)
- Accelerates the ability to effectively “triangulate” threats
- Collects and automatically correlates data across multiple security layers and tools
- Reduces dwell time from months to minutes
- Monitors all the threat vectors:
How Much Is an EDR or XDR Solution?
The cost of an EDR or XDR solution can vary based on the provider and/or the overall security strategy you’d like to use for your organization. Many companies will use more than just one solution or software to defend their data. This approach often includes an Endpoint Detection and Response (EDR) which might also have antivirus software and other security measures baked in.
With so many EDR tools available, it’s easy to get into the mindset of “buy a tool, set it, and forget it.” But the proliferation of tools doesn’t actually protect your data–in fact, it can seriously complicate your ability to identify and escalate indicators of compromise.
The cost of an EDR or XDR solution varies based on the level of security your organization requires. It also depends on whether you’re using a traditional or next-gen solution. With EDR, you’re paying to protect one vector.
With XDR, you are paying for protection across all threat vectors. A true XDR solution will provide the opportunity for tool consolidation and lower integration costs. In theory, a fully managed XDR solution is a good fit for organizations who need a full security suite, quickly, and don’t want to staff it all on their own. You’ll gain 24×7 SOC (for proactive threat hunting), have access to experts, and pay a monthly subscription cost vs the CAPEX of DIY.
DataEndure: Modern Attacks Need Modern Solutions
From a security perspective, just having tools is not enough to keep your information safe. Ultimately, organizations need to lock in on strategies and tactics that will help them get smarter with spending while insulating their security posture.
DataEndure can provide a complimentary economic roadmap, with no strings attached. We’ll provide a budget strategy for upleveling and evolving your security posture, and we’ll take into account the tools you’ve already invested in. While the cyberattacks are going up, and breach costs are increasing, your security costs don’t have to. If you’re ready to up-level your security posture, schedule a meeting today!