Whether or not you’re thinking about cybersecurity, your adversaries are. Cybercrime is a $300 billion dollar industry—and growing. We’re at a point where the speed and sophistication of the cyberattacks coming at us is outmaneuvering the security solutions on the market. The security industry is scrambling to keep up.
How did we get here? It was a convergence of factors. The rise of cryptocurrency enabled a lucrative hacker marketplace (think ransomware-as-a-service). Crypto’s anonymity and lack of centralized control made digital currency attractive to criminals. Bad actors could get paid with little risk of getting caught.
The pandemic hit and, overnight, organizations needed to support a remote workforce. Companies shifted to a cloud-first mentality to make it easier for employees to access work applications. However, the move to the cloud meant company assets were no longer protected behind a firewall, and traditional VPNs have security gaps.
But COVID didn’t just push people out of the office–it pushed out corporate data. Intellectual property and confidential data that must be protected. If you’re like most companies, your data grows more than 20% year over year.
We’re in a perfect storm of opportunity for bad actors. Crypto, a distributed workforce, the move to the cloud, exponential data growth…all these factors were at play before generative AI like ChatGPT entered the fray. While the rise in cyberattacks is staggering, it’s not surprising: 64% of all companies have experienced some sort of cyberattack. And once you’ve been hacked, there’s a mark on your back: 50% of companies that have already been attacked will be attacked again. Needless to say, cyberattacks are not a matter of if, but when.
So it’s no wonder you’re researching threat detection systems to protect your company! What you’ll quickly come to realize, though, is that there are over 3,000 security solutions out there, each touting that their product is “the best.” What they don’t tell you is that many of them only protect endpoints, such as laptops and mobile devices. With 93% of attacks starting with emails, focusing on the endpoint simply isn’t enough.
If achieving a solid security posture is beginning to feel like a Sisyphean task, don’t despair. While we’re sounding the alarm, security fundamentals haven’t changed. But this new environment requires a new approach. You need a layered defense strategy. As we break down the solutions currently offered on the market, it’s helpful to bear this in mind. Settle in, because DataEndure is serving up all the information you need to ensure your business’ survival—and, most importantly, we’ll help you develop the right mindset to keep your business protected.
What Is Threat Detection and Response?
Threat detection and response is a strategy that enables an organization to identify signs of a cyberattack and stop them before they cause significant damage. Advanced threat detection and response mixes proactive and reactive capabilities to create a layered defense system for your tech environment. Threat detection tools work by preemptively gathering information related to:
- Abnormal communication about your company’s technical environments
- Places in your tech environment that are vulnerable
- Attempts to take advantage of vulnerabilities
- Efforts to bypass security controls
- Malicious actions taken by bad actors
- Harm caused by actions taken in the tech environment
Ultimately, the goal of threat detection and response should be to reduce dwell time—the amount of time that a cybercriminal spends within your systems. Today, the average dwell time is six months. Frankly, that’s six months too long.
Why is dwell time so long? The security solutions out there are primarily focused on securing the endpoint. Unfortunately, these solutions can’t discover bad actors until they’ve already reached the endpoint. While we do need to focus on protecting the endpoint, the fact is 80% of malware comes from somewhere else: command and control procedures. Malware only needs to get to one endpoint to spread and infect other systems across the network, making your entire company their attack surface. While the bad guy only needs one small point of entry, you need to defend across every entry point—all the time.
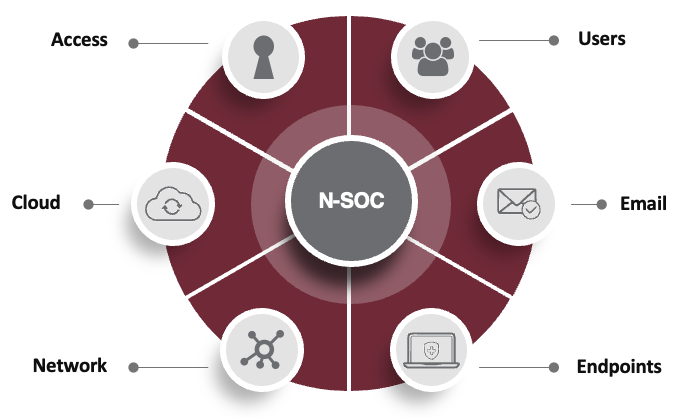
That’s why it’s vital that your company has an advanced threat detection and response strategy that stretches beyond the endpoint to protect every threat vector. You need to think in terms of layers of security as well as defenses to protect your company no matter where your employees are working from or where your data resides. You need a security strategy that can handle the new norm of distributed everything—because that’s not changing.
Common threat vectors:
Common types of attack:
- Customer Account Takeover: Hackers break into a customer’s account with your company to access sensitive personal information, such as the customer’s credit card information.
- Distributed Denial-of-Service (DDoS) Attacks: Cybercriminals prevent users from accessing your network or website by sending fake traffic to it and overloading your systems. The overload will stop your systems from fulfilling real requests.
- Malware: Software infects either individual devices or entire networks. It disrupts your company’s workflows and steals sensitive information.
- Phishing: These attacks trick users into giving up sensitive information. They typically come through emails as links to harmful websites created to resemble real ones. Users may be told to log in or to provide other personal information.
- Ransomware: This is a type of malware that locks users out of devices or whole networks until they pay the hacker’s ransom. In many cases, the hacker will not grant you access to all your data even if you do pay the requested amount.
- Zero-Day Threats: These attacks are especially dangerous because they’re completely new, thus making them more difficult to protect against. They are called zero-day threats because these attacks occur before your IT team knows about the vulnerability in your system.
Cybercriminals will throw everything they’ve got at you to find your weak point and infiltrate your business.
How Can You Detect Cyber Attacks and Respond to Them?
Protecting all threat vectors against endless attack permutations requires more than layered security. You need a layered defense strategy that extends beyond the basics to include strategy, tools, and people.
Before you put the tools in place, you need to have a plan. A comprehensive strategy encompasses each vector, types of attacks, and includes protecting the things that are important to your business. It’s about understanding the nature of the threat, understanding your regulations and market expectations, and knowing where your most valuable data resides.
The tools then map to your strategy—standing up defenses around your crown jewels. You’ll need to deploy multiple types of threat detection tools at each security layer—to provide a response tactic tuned for each type of attack. The average company can deploy up to 30 distinct security tools, all of which need to be implemented, continuously tuned, and monitored 24×7.
When we talk about that human aspect, you must have human eyes on glass, a 24×7 security operations center (SOC). None of the tools matter if you don’t have an experienced cybersecurity team trained to pick up on patterns and correlate data. The more telemetry your SOC team has, the faster they can detect and respond to threats—and reduce dwell time. This telemetry comes from the tools you have, user behavior, and gets correlated with external security industry sources (on known or emerging vulnerabilities).
Because the volume of telemetry can be astounding, security teams often face alert fatigue and burnout. A mid-sized company can generate upwards of 3 billion alerts a year. The right strategy can narrow those 3 billion alerts down to the 90 that are critical. Because a lot of the tools will alert on the same issue, you need to be able to discern the signal from the noise.
All this is a heavy lift, and you may be thinking: we really don’t have the budget or team to create all this. Most organizations don’t. Even if you have the funds to develop a 24×7 SOC, an experienced staff is hard to come by: they’re expensive, the skill set is always evolving, and it’s hard to retain talent.
With the rate of change in both tools and attacks, organizations are starting to question whether cybersecurity is part of IT or services that they should be providing on their own. It takes time to get it right, yet they need to accelerate their security now—and do so in a cost-effective way. A managed security service provider (MSSP) can alleviate the cost and burden on your IT team. Just make sure to inspect what “managed” means, so you don’t get nickel-and-dimed. Some MSPs require that you buy the tools, and you’ll be locked in to each tool’s shelf life. Some forward the 3 billion alerts to you to deal with or charge extra to handle for you. You could wind up in the same pickle you started in.
DataEndure is different. We can help you get to security maturity in 30-90 days, and we stand out from other managed services providers in our depth of experience, approach, and what’s included as part of our service. First of all, we’re veterans. We’ve got 4 decades of experience leading the way through technology change, and a lot comes with that experience. We know what it takes to secure distributed environments. We know what works together and what doesn’t.
Second, we’re tool-agnostic when it comes to the security solutions we deliver. You can leave the due diligence, POCs, and evaluations to us—we vet those 3,000 solutions to determine what’s best, and we ensure you’re always getting the best. You’re no longer in the tool business. If tool X isn’t leading the pack anymore, we use the one that is. The tools and threats are changing fast, and you don’t want to be locked into a tool that’s lost its efficacy. That’s why our approach is feature-focused, not product-driven.
While tools have boundaries of what they can and cannot do, being feature-focused allows us to quickly scale and adapt to address emerging market and security demands. Cybercriminals constantly change tactics, so we continuously innovate and adapt. We inspect, vet, test, upgrade, and pivot to keep you ahead of the curve.
Third, processes and technology are meaningless if you don’t have human eyes on glass continuously monitoring, threat hunting, and responding in real time. You’ll have the benefit of our 24×7 SOC, staffed with seasoned cybersecurity experts who handle alerts on your behalf. This is how we’re able to reduce nefarious dwell time from 6 months to 6 minutes. And the ongoing training and penetration testing we perform ensures we stay in peak form.
Everything we do is about ensuring your resilience and giving you peace of mind. This includes a proactive security stance to prevent attacks and a solid response when an attack does occur. Because the attacks show no signs of slowing, it’s critical that you accelerate your security maturity. We remove the time advantage from the adversaries and give it back to you.
What Are the Types of Detection in Cybersecurity?
There are five main types of threat detection and response solutions out there:
- Endpoint Detection and Response (EDR)
- Managed Detection and Response (MDR)
- Security Information and Event Management (SIEM)
- Network Detection and Response (NDR)
- Extended Detection and Response (XDR)
With 3,000 security tools out there, it’s a crowded and confusing market. And it’s really important to understand the differences in what, how, and who protects your system. You don’t want to find out you’re missing a feature or function after you’ve been breached, so it’s critical to do your homework ahead of time.
Remember that tools are just one part of the puzzle. Threat detection and response is a mindset, a strategy. You need processes, tools, and people—experts in a 24×7 SOC—working in concert to truly protect your business. That said, let’s take a closer look at each of these solutions (we saved the best for last).
What Is EDR?
Work from anywhere means your people, devices, and data are out in the wild. Because cybercriminals target the endpoint, there’s pressing urgency for endpoint detection and response (EDR) solutions. EDR continuously monitors endpoints. In theory, endpoint detection and response tools deliver real-time detection and remediation of complex threats with no need for human intervention.
Many people have a hard time distinguishing EDR vs antivirus tools, and for good reason. Antivirus solutions were the precursor to EDR, and many EDR players out there are former antivirus solutions. People have moved away from traditional antivirus because it’s inadequate—while it looks for changed files, it doesn’t look for behavior. EDR is way more advanced because it looks for changes in behavior, anomalous patterns, not just changes in file signatures. Unfortunately, many EDR providers have tried adapting their 20 year old antivirus solution rather than building something new, so they have baked in limitations. So, if you’re evaluating an EDR solution, be sure to bear this in mind.
Questions to ask:
- Is the solution based on legacy anti-virus?
- Does your solution include both SOC analysts and incident responders?
Today’s workers, distributed environments, and data demand a different approach, not a band aid solution. You need an EDR solution purpose-built to defend against sophisticated threats. DataEndure’s EDR includes:
- 24×7 security operations center (SOC)
- Multiple security layers such as: attack blocking, patching, exploit blocking, firewall, whitelisting/blacklisting, full category-based blocking, admin rights management, and a next-gen Antivirus.
- We capture important system events such as registry and file changes and use real-time behavioral monitoring to pinpoint suspicious activity.
- Furthermore, we employ machine learning algorithms designed to spot yet unknown malware types, which will subsequently make behavior-based categorization decisions.
- Critical to all of this is 24×7 expertise: threat hunters to monitor and respond to threats.
What Is MDR?
Managed detection and response (MDR) detects and responds to security issues across your endpoints and network. There are two flavors of MDR. One is you buy the tool and the MSSP manages it. The other is you get the solution from the MSSP, but it’s typically one size fits all.
If you’re evaluating an MDR solution, make sure you ask these questions:
- Do I buy the tools or use yours?
- Does this include a SOC?
- To what extent does this protect the network?
This type of threat detection system most appeals to companies that haven’t made a major investment in IT. If you don’t have a big IT team, or you don’t want to dedicate your team to cybersecurity, this could save you time and money versus building and maintaining an in-house solution. It will be a boon to your business and a kindness to your staff: 79% of IT professionals experience alert fatigue because they can’t keep up with the volume of alerts coming at them.
As we previously mentioned, some managed service providers will charge you extra to handle alerts on your behalf. By contrast, what DataEndure includes in our MDR solution is unique in the market. Our fully integrated MDR solution includes:
- 24×7 security operations center (SOC)
- Distributed endpoint security
- Distributed network security
- Vulnerability assessment
- Security controls validation (Purple Teaming)
- 365 days threat incident history
- Integrated intelligence and MITRE ATT&CKⓇ threat indicators
What Is SIEM?
Security information and event management (SIEM) supports threat detection, compliance, and security incident management by spotting abnormal behavior and potential cyberattacks. The SIEM ingests and aggregates an immense amount of data from multiple systems (network devices, servers, domain controllers, all systems in your threat vectors) and analyzes the data. Gartner identifies three critical features for SIEM: threat detection, investigation, and time to respond.
Common features may include:
- Basic security monitoring
- Advanced threat detection
- Forensics & Incident Response
- Log collection
- Normalization
- Notifications and alerts
- Security incident detection
- Threat response workflow
SIEM tools provide insights into where threats exist, but unless you’ve got a SOC and a methodology for understanding the data so you can identify a threat, it may as well be gathering dust on a shelf. You need to be able to monitor effectively, staff appropriately, and take action quickly to harness the power of a SIEM. If you have a guard tower, but only have a guard on watch one day a week, consider all the threats that get missed.
If you’re evaluating a managed SIEM solution, be sure to ask:
- Do you have a 24×7 SOC?
- How are alerts handled? Do you have automation, and what does it include?
- When you identify an issue for one customer, does it get addressed for all customers?
- Are you incorporating data from industry sources like MITRE ATT&CKⓇ?
- Do you charge us for ingested data–or solely processed data? (You could be paying for a lot of data that’s not meaningful).
DataEndure makes it easy to get the full value out of SIEM and then some. To start, we make the investment in the tools, people, and training—not you. You get a guard tower that’s staffed with a highly trained battalion of threat hunters around the clock. Next, we apply learnings from one customer to all our customers. That means when we spot something dangerous happening for one client, we proactively address it for all clients—we’re not waiting until we find it elsewhere. There’s also the benefit of us ingesting industry data from MITRE ATT&CKⓇ (Adversarial Tactics, Techniques, and Common Knowledge), which documents new vulnerabilities and attack surfaces as they emerge.
What Is NDR?
A cyberattack can’t happen without a network, so you’d think the network would be front and center as far as security priorities. Unfortunately, it’s not. And, in the new world of distributed everything, the network is even more vulnerable as a target.
Network protection is critical to threat detection cybersecurity, and Network Detection and Response (NDR) serves as an early warning system, continuously monitoring network traffic to identify anomalies or suspicious activities. Attackers are constantly changing their strategies to evade detection; NDR’s rules-based detection, behavioral modeling, and machine learning helps you detect them faster. Remember, this is all about dwell time and taking the time advantage away from the bad actor. Each time you can detect and block the adversary before they get to the endpoint, it’s a win.
So what’s the problem? The world has changed, and the network hasn’t.
There’s no longer a secure edge; remote employees aren’t behind a firewall. IT teams not only have to worry about security on their own network, but on the networks at employees’ homes and WiFi locations. Threats can enter your network as simply as:
- Personal devices connected to your home network get infected.
- If those devices are considered trusted, the infections on them are also trusted.
- Boom! You’ve mainlined viruses.
And, if your employees are using VPNs, we’re sounding the alarm bells. To put it simply, VPNs don’t inherently provide the security and safety they are touted to provide. Sure, once the tunnel is established, any traffic traversing the tunnel is encrypted (although not always with a secure protocol). But what VPNs don’t provide is protection against malware, spoofing, phishing, man-in-the-middle (MITM) attacks, etc. VPNs also start with the premise that the user is trusted, meaning they don’t recheck devices after they’re connected to the network. VPNs authenticate a machine to entire network segments—one time. With the threat actors present today, VPN cannot and should not be relied upon as a viable means of securing data streams for businesses.
We’ve got to change the way we treat people who connect to the network and the way we monitor the network.
Through DataEndure’s Zero Trust Network Access (ZTNA), devices connected to your network must prove that they can be trusted. If an employee’s device doesn’t meet certain requirements related to where, what, or when the network is being accessed, as well as other factors, then they can’t access the network. ZTNA better protects your network from threats than traditional VPN or firewalls do.
What Is XDR?
We’ve saved the best for last. Extended detection and response (XDR) goes even deeper, combining security measures to provide a comprehensive layered defense for next-level threat detection and response.
The concept behind the “X” in XDR is to close security gaps across all threat vectors (like endpoint, network, cloud, etc). Think of XDR in terms of a castle during a battle. It will provide you layers of security to keep threats out, like the moat around the castle and tall walls. Beyond this, XDR adds layers of defense to provide a response tactic tuned for each type of attack coming at you. It’s your archers, swordsmen, and hand-to-hand combatants. The goal is to pick off attackers, reduce their army, so you can take most of them out before they even reach the castle walls. The fewer adversaries who breach the wall, the better poised you are to quickly neutralize them.
The solutions out there are defending against what gets in. They’re looking for a changed file or a change in behavior. DataEndure’s strategy is to take out bad actors before they get to the endpoint.
For example, today’s distributed environment is too complex and sophisticated for yesterday’s threat detection and response tools such as lightweight gateway email and firewall solutions. That’s a huge gap given that these are some of the main attack vectors cybercriminals use to get to the endpoint. In fact, 93% of attacks start with email, and phishing schemes have become more advanced. Without coverage for these critical vectors, you’re relying on your users to be your first line of defense.
The other underprotected vector is the network. It’s not about VLANs and firewalls. Standard segmentation isn’t something that you can set and forget. It’s something that is evolving, continuously changing, and easily breaks. The minute you add a new application to your stack, modify an application, need two applications to talk to each other, or move a server to the cloud, you’ve created a hole in the network and expanded your attack surface.
The advantage of DataEndure’s XDR solution is having an “X” that is dynamic. As vectors adapt and toolsets change, the solution has the flexibility to reinforce and bolster protection for that vector–delivering the highest level of security at any point in time.
If you’re evaluating an XDR solution, be sure to ask:
- Do you have a 24×7 SOC?
- How do you respond to new cyberattack tactics?
- To what level do you analyze and protect email? (Gateway email security isn’t enough!)
- What defenses are in place for DNS protection? (Firewalls can’t cover distributed workers)
- How fully integrated are the layers (is this a seamless solution)?
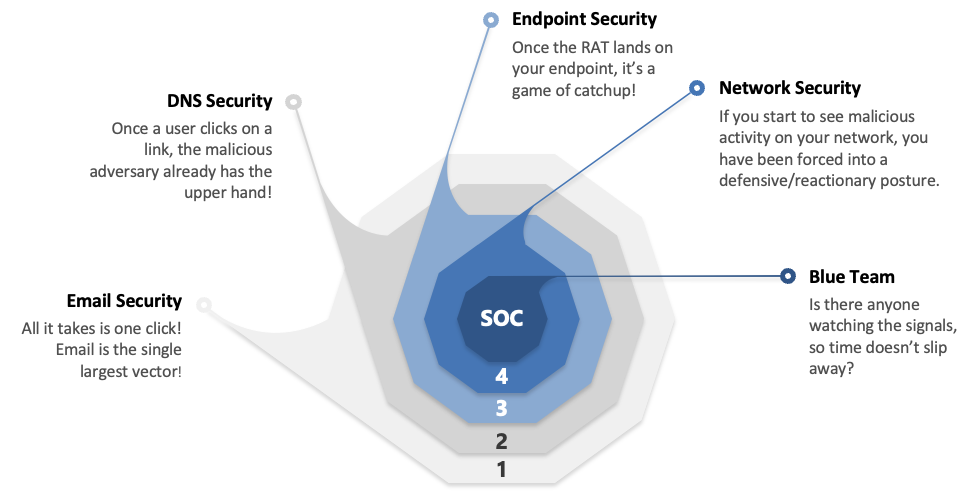
DataEndure’s XDR delivers 5 layers of protection. Why is this significant?
- 3 of the 5 layers reduce the load on the endpoint
- Gain the greatest amount of telemetry
- Accelerate your ability to detect and isolate adversaries
- Dramatically reduce dwell time
- Includes the network, access, email, and endpoint vectors
What Is the Difference Between EDR and XDR?
EDR and XDR are not created equal. The difference is in the “X”.
While XDR evolved from EDR, EDR’s biggest drawback is that it focuses strictly on endpoints. With more and more people using the cloud and virtual private networks, EDR leaves these spaces wide open for attack.
When choosing an XDR solution, be wary of companies that say they provide all-in-one XDR solutions. Many start from an EDR solution, tack a few features on, and call it XDR. They start with EDR as their baseline, which is the wrong approach with so many companies working virtually or hybridly now. Cyber attackers don’t typically start by attacking the endpoint, so why should your threat detection and response solution protect that first?
When it comes to EDR vs XDR solutions, XDR should protect both what EDR can and what it can’t. That’s DataEndure’s approach anyway. Our XDR has more telemetry, allowing it to collect and analyze potential threats from a wider variety of sources. Plus, DataEndure’s XDR offers your company a chance to segment your network so that bad actors have a harder time accessing all your data. Not only that, but many of the steps that XDR takes to protect your systems can be automated, whereas those of EDR typically can’t.
What’s more, and we cannot emphasize this enough, many of these companies won’t come with a full-service SOC. Without your layers of defense, your layers of security aren’t as strong. DataEndure provides an XDR solution including a 24×7 SOC staffed by experts who actively protect your network, endpoints, and systems.
What Are 4 Methods of Threat Detection?
The 4 ways to detect a cyber attack are:
- Threat Intelligence: Cybersecurity tools collect and analyze data from past and present events to detect similar attacks against your system and to show you where your systems might have vulnerabilities.
- Attacker and User Behavior Analytics: This method looks internally to spot unusual user-specific behavior and/or behavior in your network overall to identify threats.
- Intruder Traps: Cybersecurity teams create bait, called honeypots, to attract intruders within your systems. Once the attacker falls for it, the teams will be alerted and take action.
- Threat Hunts: This method works on offense rather than defense. IT professionals use the methods we’ve already discussed to actively search your tech environment for intruders. You’ll need a skilled SOC to take on this challenge.
There’s no single magic bullet. To get on secure footing, you must employ a combination of these methods. DateEndure’s managed security and managed infrastructure can help get you more secure, faster. Your company will gain the expertise needed to protect and prevent ongoing attacks, so you’ll not only survive, but thrive.
How Do I Set Up TDR?
Simply put, with DataEndure’s managed security services, you can be up and running in 30-90 days. You gain the time advantage against threat adversaries.
To set up your own TDR, you need: strategy, budget, expertise, and time. This can get complicated quickly, especially if you don’t have an existing IT team or if you have a small one. The alternative many organizations are choosing is to consume security services vs build them in-house. Doing so accelerates your time to security maturity, significantly reduces costs, and allows you to stay focused on your business.
You didn’t get into business to be a security expert, but we did! DataEndure has no hidden agenda when it comes to providing our customers with cybersecurity solutions. We have a single goal—your business’ success. Our company has been around for four decades, and we’ve grown up with all the cybersecurity technologies. We use this knowledge to inform the solutions we deliver, and we focus on what’s important, dwell time. In fact, while the industry average is 6 months, for our customers, it’s six minutes.
DataEndure’s solutions are layered, meaning if one fails to protect your environment, there’s another one in place to stop an attack. What’s more, you will receive ongoing vulnerability assessments at no additional cost when you work with us. Don’t have a 24×7 SOC and cybersecurity team? No worries! That’s why we’re here.
And, we don’t stop there. Just as cyber criminals are always advancing, we’re constantly researching and exploring new technology and services to keep one step ahead of those bad actors—remember, cybersecurity is a mindset, not a set-it-and-forget-it!
Ready to discover where your company’s tech environments are at risk and could use some extra protection? Check out one of our complimentary health checks to get started: