Whether you’ve got regulatory requirements or you’re simply trying to acquire cyber insurance, you need to demonstrate that you’ve got a solid security posture in place. Simple, right?
A quick search for “threat detection and response tools” will quickly leave your head spinning, especially if you’re not a cybersecurity expert. There are literally thousands of solutions, and each one promises the moon…but they can’t all deliver, especially when the majority are only focused on endpoints (like laptops, mobile devices, and servers) . But criminals don’t just target your devices. In fact, 93% of attacks start with email.
What the security vendors won’t tell you is security isn’t a tool set, it’s a mindset. You need a layered defense strategy that protects your vital threat vectors, meets your regulatory or compliance needs, and protects your most valuable data no matter where it resides.
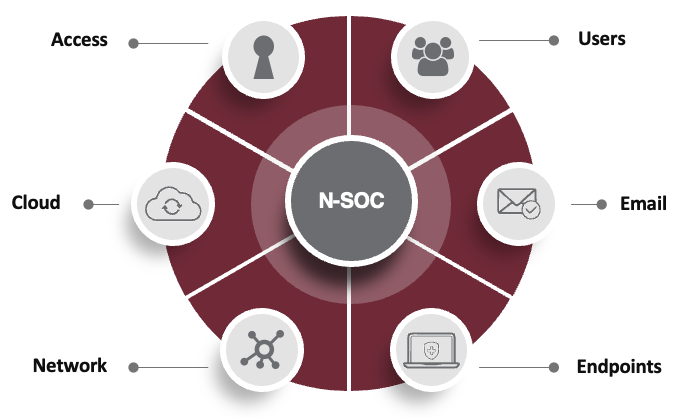
These are the key vectors you need to defend:
Let’s explore some common questions:
- What are the four 4 main types of security attacks commonly observed?
- What are the endpoint detection methods?
- What is an endpoint response tool you can use for security?
- Is an antivirus an EDR tool and is a firewall an EDR tool?
- What are the best threat detection and response solutions?
What Are the 4 Types of Threats?
As you’re building your security strategy, it helps to understand what you’re defending against. Four of the most common forms of cyberattacks are malware, ransomware, distributed denial of service attacks (DDoS), and phishing. For any attack, there’s a broad ripple effect that impacts not only the security of your business and data, but the security of your customers and suppliers as well. For example, they may lose money, damage their brand, or face legal consequences.
Things are even more dire when you consider cyber criminals are constantly adapting their techniques and shapeshifting their approaches to avoid being detected. It’s crucial for your business to stay informed about new threats and adapt to the dynamic nature of these adversaries.
Malware
Created with the intent to cause damage to a computer, network, or other device without the owner’s permission or knowledge, malware has grown up since the early days of the internet…it was effective then, and even more so now. Fast-changing polymorphic malware now makes up 97% of the malware organizations face – updating itself with new definitions every few days, mutating faster than traditional security systems can keep up and making previous detection signatures (or traditional antivirus solutions) obsolete.
Phishing
Did you know that 93% of attacks start with email? Phishing is an attempt to trick a user into downloading malware, disclosing private information, or visiting a malicious website. Over the past few years (exacerbated during the pandemic), phishing attacks increased over 600%. Unfortunately, there are many phishing tactics and it only takes one click, download, or infection for the bad actors to get in. And once this happens – game on!
While gateway-based email solutions are essential, they’re not comprehensive protection against advanced threats–they only protect users from 3 out of 13 email borne threats (spam, antivirus scanning, and content filtering). If it sounds like the deck is stacked against you, it doesn’t have to be. Advanced phishing protection (APP) complements a gateway solution to deliver a layered defense. APP provides protection from the 10 remaining attack vectors (account takeover, lateral phishing, conversation hijacking, domain impersonation, business email compromise, blackmail, service impersonation, scamming, spear phishing, and URL phishing).
Essentially, you need a layered defense when it comes to phishing—blocking attempts and eradicating bad actors when a breach occurs.
Ransomware
Ransomware encrypts a user’s or organization’s files and holds them captive until a ransom is paid. These attacks are on the rise: one survey found that in 2022, 76% of respondents experienced a ransomware attack. In part, the rise of cryptocurrency has emboldened these attacks—as there’s more certainty that criminals will get paid and not get caught. Organizations need to prepare for a ransomware attack as a “when” scenario—not an “if.”
And the “when” can be devastating and gets worse as the clock keeps ticking. When companies fall victim to ransomware, they risk losing valuable data and suffering significant financial losses. Additionally, the longer bad actors have access (also known as “dwell time”), the more they will spread across your entire network and wreak havoc.
Ransomware can become an endless costly cycle that disrupts business continuity. Of those who pay a ransom, many don’t get their data back in a usable state. What’s more, 80% of ransom victims suffer repeat attacks.
Distributed Denial of Service (DDoS) Attacks
A distributed denial-of-service (DDoS) attack is an attempt to block legitimate users on a server, service, or network by flooding it with so much internet traffic that the infrastructure is unable to manage it. Imagine all of your business’ critical operations coming to a screeching halt. DDoS mitigation solutions that businesses can use to enhance the security of their data and users include network detection, response, routing, and adaptation.
What Are Threat Detection and Response Priorities?
The attackers employ a number of attack tactics, so it’s important that you have a layered security strategy. One that is both proactive and reactive–the goal is to minimize the amount of time an adversary is in your system, called dwell time. At every layer, you should be able to identify a threat and have security measures that kick in to stop the attack in its tracks. And importantly, every method relies on the pairing of the technology + human expertise.
Priorities for an effective threat detection and response plan:
- Monitor the Ecosystem: Implement a wide variety of tools and technologies to keep tabs on network traffic, endpoints, and other crucial systems.
- Detect Threats: Use analytics and machine learning algorithms to look for unusual behavior that could suggest an attack.
- Investigate the Threats: Launch an investigation to determine the reason for and extent of the breach.
- Mitigate the Issue: Isolate the compromised systems, limit network activity, or install security patches in order to restrain the impact and eliminate the threat.
- Restore Business Operations: Depending on what was compromised, get everything up and running (infrastructure, access, data, etc).
- Test and evaluate: Continuous testing and evaluation of security controls to validate the efficacy of your security tools and change out as necessary.
What Are 3 Methods of Threat Detection?
The goal of threat detection must be centered on minimizing dwell time. Yet, given all the tools available, the average dwell time remains 221 days–that’s 221 days that bad actors are undetected in your environment. What gives?
As you look to solve your security challenges, dwell time needs to be your benchmark for evaluating security tools and services. Make sure they can answer “in what form or fashion will this reduce my dwell time?”
Threat detection can be implemented in a number of ways, but here are three of the most typical methods:
1. Analyzing User and Attacker Behavior: Users’ actions are monitored and analyzed to spot any unusual behaviors that might suggest malicious activity on the system. If a user’s behavior is concerning, their credentials might have been compromised.
2. Detecting Anomalies with Machine Learning: Machine learning (ML) can find unknown malicious actions when done with a well-trained model. ML is used to teach the system to recognize an established baseline rather than looking for previously identified threats.
3. Evaluating Signatures of Bad Actors: Signature-based threat detection includes the use of both indicators of compromise (IOCs) and characteristics of previously identified threats. An IOC could be a malicious site, a recognized code sequence, or a pattern of activity that typically indicates a hostile network attack.
If you want to protect your environment from known and unknown threats, you need to think about security as a multi-layered approach. While there are different types of threat detection, it requires a combination of strategy, tools, and human experts to establish a robust security posture. If you’re looking for threat detection tools, bear this in mind. At the end of the day, the threats are dynamic, so your solution needs to be as well.
What is EDR?
There is an understandable focus on the endpoint given the distributed nature of employees and the devices we use to work (home office, cloud, laptops, mobile phone, servers). Endpoint Detection and Response (EDR) or Endpoint Detection and Threat Response (EDTR) has been positioned as a silver bullet; however, most EDR solutions neglect the network. This is the key onramp to the internet and leaves a huge security gap that adversaries are happy to walk through.
What is an Endpoint Response Tool?
Security experts use endpoint response tools to detect and stop cyber attacks on endpoints, like laptops, desktops, servers, and mobile devices. These devices are particularly vulnerable to attacks, so protecting the endpoint against malicious actors makes sense.
But with over 3,000 security tools out there, it’s important to understand the features and functions that are critical to defend your endpoints.
- Attack Blocking: Attack blocking identifies and blocks malicious behavior by protecting endpoints from both known and unknown types of illicit cyber activity. Typically, attack prevention capabilities rely on behavior-based analysis, which involves monitoring endpoint activity for obvious signs of suspicious or unusual behavior.
- Patching: The newest security patches and updates can be installed on endpoints with the help of patching. The process of patching addresses vulnerabilities that could be exploited by hackers.
- Exploit Blocking: By detecting and blocking vulnerabilities in programs or applications on endpoints, exploit blocking can stop attacks from both known and unknown threats.
- Firewall: By monitoring every connection passing through a network, firewalls help stop hackers from gaining access to sensitive data and systems. With the network edge moving out, firewalls don’t have the efficacy they once did (when everyone was working on premises).
- Whitelisting/Blacklisting: A whitelist or blacklist is a set of permitted or restricted files, folders, or websites. Whitelisting allows only trustworthy software or apps to run whereas blacklisting blocks the use of known viruses and malware.
- Full Category-Based Blocking: Category-based blocking allows you to restrict access to groups of programs or apps that have similar features. This function is capable of blocking access to potentially dangerous or unapproved resources from within endpoints.
- Admin Rights Management: Make sure that only approved users have access to protected system resources by managing and restricting administrator permissions for endpoints.
- Next-Generation Antivirus (NGAV): To identify and stop threats, NGAV employs a number of cutting-edge techniques, including behavioral analysis, machine learning, and others.
Endpoint detection and response is certainly one component of an advanced layered defense; however, it doesn’t go far enough.
What Is an Example of an EDR Tool?
The best EDR tool your business can use is actually not a tool. After all, the efficacy of tools changes over time, especially with such a dynamic adversary. What was a market leader yesterday is unlikely to lead the market tomorrow; so organizations need to be able to have a dynamic tool set—which is hard to achieve if you are in a “build it yourself” situation. You evaluate tools, buy them, integrate them, staff/train around them…then when the tool has to change, you wash, rinse and repeat.
Sound exhausting and confusing? Yep, it sure is. That’s why managed security services are growing in adoption. For example, DataEndure can do the heavy lifting for you—after all, we’ve got 4 decades of experience in securing distributed environments. Our tool-agnostic approach means that we’re constantly vetting those thousands of solutions to find the ones that work for your current and future needs. When, not if, those needs change, we’ll change right along with it and ensure you’re getting the best. After all, if cybercriminals are constantly shifting, the only way to stay one step ahead is to beat them at their own game. That’s why our approach is feature-focused, not product-driven with continuous innovation and adaptation.
What Is EDR vs XDR?
Endpoint detection and response (EDR) and extended detection and response (XDR) are two types of security solutions. Let’s start with what they have in common. Both of them find, investigate, and respond to threats on business endpoints.
While the endpoint is the goal for many bad actors, there are many different threat vectors adversaries have available, the endpoint is only one of them. In contrast, XDR provides comprehensive protection including all the threat vectors (cloud, network, endpoint, and beyond). This layered approach has different levels of security working in tandem to proactively block adversaries from getting in and quickly eradicating those who do.
Stay One Step Ahead of Cyber Attacks with DataEndure
You didn’t get into business to be a security expert, but we did! DataEndure helps your business become digitally resilient and stay that way in the face of rapid change, growing complexities, and evolving threats. We have no hidden agenda, just a single goal—your business’ success. We’ve been around for four decades and security has been foundational to who we are since our inception. This experience informs how we build, manage, and evolve our security services.
If the tools-centric approach has either failed you or frustrates you, you’re not alone. Let’s talk about how a feature-focused managed security solution can accelerate and simplify your path to security maturity. Schedule a meeting today.