Chief Marketing Officer
The ability to quickly and effectively respond to threats is an essential ingredient of any modern cybersecurity strategy. As the digital landscape continues to evolve, businesses are at risk because cyber criminals are able to bypass older security protocols. In fact, the average total cost of a ransomware breach has reached $4.62 million, according to IBM.
Traditional tools are set up to respond after a compromise has occurred. The mindset was to be ready to respond “if” something happened. With the nature of cybercrime today, it’s no longer if, it’s when.
Because all organizations are equal targets, having preventive threat detection and response measures in place to reduce the likelihood of a compromise is as important as having the ability to respond. When you know something is going to happen, you invest in preventive care.
A true endpoint detection and response (EDR) platform is an accelerator to help you on both sides of that fence.
What Is Endpoint Detection and Response?
Endpoint detection and response (EDR) is an endpoint security solution that combines real-time monitoring and data collection from endpoints with automated response and analysis capabilities. EDR is one of several types of advanced threat detection and response tools that leverage emerging technologies like artificial intelligence, behavioral analytics, and continuous incident response to help identify and eradicate threats.
Key functions that an EDR security solution should perform include:
- Collect telemetry from endpoints that connect to the company network (from laptops, mobile phones, servers)
- Analyze gathered data to detect threat patterns and isolate threats
- Alert security team of indications of compromise
- Remove or contain threats that evade security measures
That being said, the benefits of endpoint detection and response are limited. That’s because EDR is focused on endpoints—and not threats across the broader network. Given the fact that there are 5 other vectors that need protection, there’s a heightened need for a more comprehensive solution.
What Is XDR?
The next evolution in security, extended detection and response (XDR), represents a transformational shift in how organizations defend and protect their digital assets. Instead of a tool for this and a tool for that, XDR offers a comprehensive coverage across all threat vectors including the endpoint.
An XDR solution should provide:
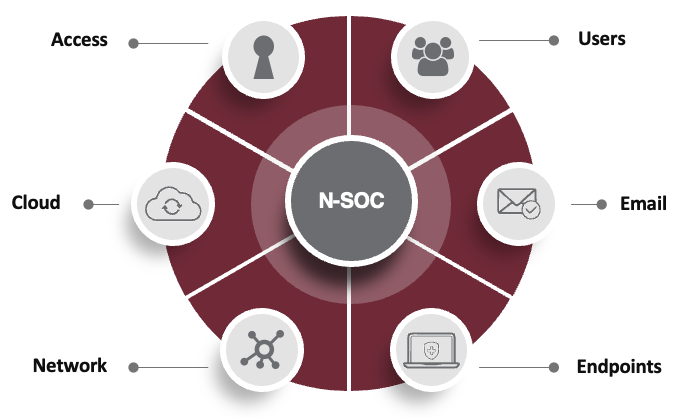
- Layers of protection across your entire environment (network, cloud, access, email, endpoints, users)
- Response tactics fine-tuned for each type of attack
- 24×7 security operations center (SOC) trained to pick up on patterns and correlate data to thwart nefarious actors.
- Singular visibility across all vectors to quickly assess areas of risk
- Monitoring, alerting, and remediation
- Continuous incident response
- Active threat hunting
- An evergreen security platform to ensure your security controls are best in class
What Are the Advantages of Endpoint Detection and Response vs XDR?
Organizations, especially those with a large number of vulnerable endpoints, can benefit greatly from incorporating endpoint detection and response tools into their security strategy. It’s important to understand the benefits of endpoint detection and response are limited and only protect 1 out of 6 vectors.
The differences between EDR and XDR are significant because of what they cover. XDR is more extensive, fully protects all 6 threat vectors across an organization. By consolidating visibility and threat management into a single solution, XDR can greatly optimize your business’s security posture and significantly accelerate your ability to detect, investigate, and respond to threats.
Through the integration of human expertise, process, and best-in-class technology—XDR is able to:
- Enhance visibility across your environment
- Gather and correlate data
- Detect anomalous behavior
- Eradicate threats
- Minimize dwell time (the amount of time a bad actor is undetected in your environment)
Accelerated XDR Solutions with DataEndure
At DataEndure, it’s our priority to minimize the time an adversary has to do damage in your environment. To do this, it requires vigilance across every threat vector in your environment. That’s our specialty. With an average dwell time of just 6 minutes (compared to the industry standard of 6 months), we put the time advantage back on our customers’ side.
Digital resilience is our core business, and we’ve been helping our clients survive and thrive through any kind of change, challenge, and compromise for four decades. Our managed security service can help you:
- Accelerate your security maturity (30-90 days)
- Lower costs (50% less than doing it yourself)
- Attain an evergreen security solution
- Gain 24x7x365 experts to monitor, alert, remediate, and restore
- Reduce dwell time to minutes vs months
To learn how we can help you accomplish your security objectives, let’s talk.