Chief Marketing Officer
Threat protection and threat detection are two essential elements of cybersecurity. “Protection” focuses on stopping threats, while “detection” is all about finding them. But neither protection nor detection can exist in a vacuum. The two have to work together—along with other strategic elements—to be effective. In fact, good threat protection is predicated on proper threat detection. And threat detection is meaningless without a way to protect one’s assets.
Proper threat detection and response must be part of your plan, and it needs to be based on a solid understanding of cybersecurity threats and solutions. This year’s 2023 Verizon Data Breach Investigations Report confirms what many organizations are already experiencing: attackers continue to change the threatscape. Despite increased spending, breaches are more frequent, more sophisticated, and more expensive. The key takeaway is cybersecurity must not be a “set and forget” concept.
You can’t just buy threat detection tools and expect them to do all the work. You need an integrated, unified approach that doesn’t leave your security to chance. And, interestingly, the most important part of your defense strategy isn’t digital at all: it’s the people. You need experts who monitor the tools, correlate the data, proactively threat hunt and restore business operations.
A lot of the tools out there kick into gear after a breach has happened. As important as that is, you have to shift your mindset to assume something will happen and not just wait until it does.
What Is Threat Detection and Prevention?
In cybersecurity, the concept of “threat detection and prevention” is about identifying malicious activity and stopping it before it does damage. A successful threat detection and prevention strategy encompasses both proactive and reactive elements. In the best scenario, you repel the attacker so they can’t gain a foothold. For those who do evade detection, you want to minimize their ability to do damage.
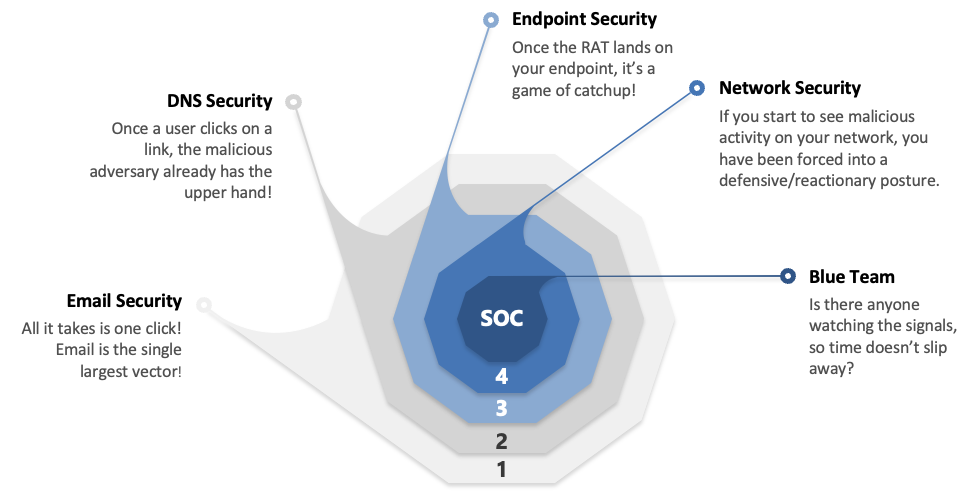
The ultimate goal is to reduce dwell time, or the amount of time hackers spend in your environment. For reference, the average dwell time is six months—and yes, that’s as bad as it sounds.
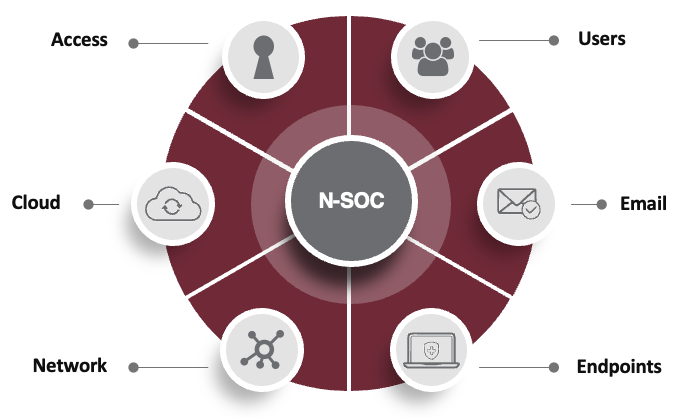
But before you rush to buy threat detection tools, there’s something you should know: most tools out there miss the mark. Why is that? For one, many only focus on endpoint detection. While it’s important to monitor endpoints (the devices that connect to your network, such as computers), endpoints are just one of six vulnerabilities across the enterprise. This means at best, you’re covering about 17% of your points of compromise.
The best cybersecurity guards all six of the following vectors:
Even when businesses buy the right tools, they’re usually ill-equipped to reap the full benefit. They either lack the integration, staffing, or expertise to pull together and maintain a robust security posture in a dynamic threat landscape. The ability to monitor and respond 24×7 is no longer a nice-to-have, it’s a requirement today. Cybercriminals don’t operate on business hours, so you have to be vigilant around the clock.
Given the challenges, let’s answer the question: what is threat protection done right?
What Is Advanced Threat Protection?
Advanced threat protection needs to focus on three areas:
- Early detection: halting attacks in progress or mitigating threats before they breach systems
- Robust protection: disrupting activity in progress or countering actions that have already occurred as a result of a breach, and
- Swift response: Interrupting the lifecycle of the attack to ensure that the threat is unable to progress or proceed
To do this, advanced threat protection must work across all threat vectors including endpoint, network, email, cloud, access, and users. Also, human intelligence must be a component of a layered defense strategy for 24×7 monitoring, threat hunting, and remediation.
Done right, advanced threat protection begins with strategy, expertise, and then tools. There’s a lot that goes into a comprehensive approach. For example, DataEndure’s advanced threat protection strategy includes:
In the same way a castle has multiple lines of defense—a moat, gate, archers, and riders beyond the wall—DataEndure delivers layered security to protect our clients. We don’t just keep threats out; we stop them before they strike, and hunt them down where they camp.
DataEndure: Cyber Threat Prevention at Its Best
If you’re a business, cybersecurity is not a luxury—it’s a necessity. Adversaries are a real threat that every business must be ready to square off with. You need a security strategy that drives vigilance, resilience, and continuous adaptation to evolving threats.
That’s how we at DataEndure protect our clients. We know security, and we’ve got over 40 years of success to show for it. Our managed security solutions ensures that you’re prepared to defend against not just today’s adversaries, but tomorrow’s. Let’s talk today about what advanced threat protection looks like for your business.