Chief Marketing Officer
Cyberattacks are the most nefarious and organized threats modern businesses face. With cyberattacks happening every 39 seconds, taking calculated measures to detect and neutralize threats before your systems are compromised is of the utmost importance. This is where threat detection and response comes into play.
- Threat detection is the ability to quickly and accurately identify threats to the endpoint, network, applications, or other assets.
- Threat response is the mitigation efforts used to neutralize and prevent cyber threats before they compromise the business.
Ideally, threat detection and response solutions empower organizations to quickly identify indications of compromise and respond to any active threats before irreparable damage is done. Think of it this way—cyberattacks are inevitable, but a total breach can be prevented. The main objective of threat detection and response is to decrease dwell time—aka how long a cybercriminal is in your system undetected to do recon and damage.

Advanced threat detection and response solutions, on the other hand, combine proactive and reactive functionalities to cultivate a multi-layered defense system. These solutions work by gathering critical telemetry indicating:
- Suspicious or anomalous behavior
- Vulnerabilities in your digital ecosystem
- Adversarial attempts to thwart your security
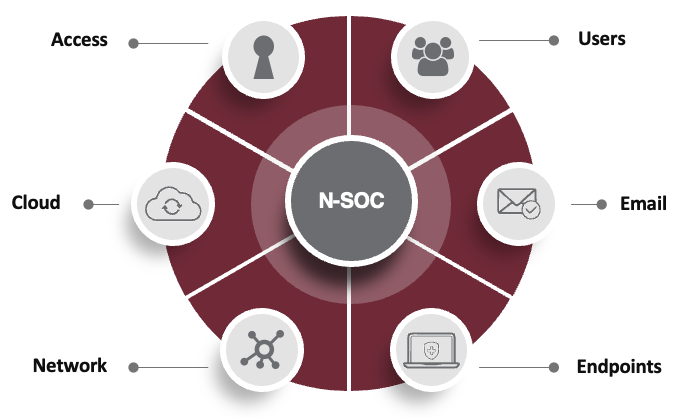
An advanced threat detection and response strategy extends beyond endpoint detection and response (EDR) to guard and monitor all threat vectors. Your strategy should encompass integrated layers of security at each threat vector to protect your organization regardless of where your employees are, how they’re accessing data, and where that data resides.
Common Threat Vectors
Why Is Threat Detection Important?
Threat detection, and cyber security in general, must be high on the list of priorities for any modern business. The global average cost of a data breach reached $4.35 million in 2022—the highest number ever reported in IBM’s The Cost of a Data Breach Report. For many businesses, the cost of a breach is too much to bear. And, by all accounts, the rate of cybercrime will continue to increase. In short, businesses are operating in shark infested waters. The challenge is to catch the wave that will take them through dangerous conditions.
What Are the Four Types of Threat Detection?
As you consider how to identify threats and vulnerabilities, these are four most common types of threat detection:
- Threat intelligence collects, correlates, and analyzes data providing critical telemetry to help quickly assess a threat actor’s motives, targets, and attack behaviors.
- Attacker and user behavior analytics looks for deviations or anomalies from expected user patterns. It focuses on what the user is doing–apps launched, files accessed. etc. A combination of AI and human intelligence looks for behavior that deviates from an established baseline.
- Intruder traps, often called honeypots, are digital bait used to attract intruders. These are used as a preventive measure to identify vulnerabilities before a real attack occurs. It’s part of testing your defenses. When the attacker falls for the bait, you get insights into where you need to shore up your defenses.
- Threat hunts are critical because no security tool is 100% effective. Security experts proactively look for and root out cyber threats that have secretly penetrated their network. Threat hunting is a combination of ongoing research and proactive monitoring and inspection of anomalies before they turn into a full breach.
Ultimately, you cannot rely on a single threat detection method for complete protection—you must use a layered defense strategy. For example, DateEndure’s managed security services integrate best-in-class tools, expertise needed to protect and prevent ongoing attacks.
For True Prevention and Protection, Consider XDR
Cybercriminals are constantly developing new tactics and technologies to thwart existing security measures. And conventional threat detection and response falls short in terms of breadth and depth of protection against today’s threats. Extended detection and response (XDR) promises layered protection across threat vectors—delivering complete security at any point in time.
The benefits of an XDR defense are twofold:
- XDR provides layers of security to keep threats out.
- XDR applies the right defensive tactic based on the type of attack.
XDR is not a single tool, it’s a new approach. XDR unifies best-in-class security tools and data sources into one platform. You need to know what’s going on across your threatscape to understand how and where to best defend the business. With enhanced visibility across your environment, you’re able to identify threats faster and accelerate your defense. And to get full value of the solution, you need a 24×7 security operations center (SOC) with expert eyes on glass to analyze, correlate, and orchestrate your defense.
A Simple Approach to XDR
While deploying security solutions can be expensive, time consuming, and complicated–they don’t have to be. DataEndure’s managed security services make it easy to take you from where you are today to security maturity.
Here’s what our customers experience:
- Bad actors are booted in 6 minutes. DataEndure takes the time advantage away from the adversary, reducing dwell time to 6 minutes vs 6 months (industry average)–this is the game changer.
- An accelerated path to security maturity (30-90 days vs months to years)
- Significant cost and time savings. There’s no more need to constantly evaluate tools and deal with purchase cycles.
- Gain access to a pool of talent, resources, and expertise that are unmatched. Our depth of experience, unique approach, and XDR capabilities make us different —dare we say better—than other security providers.
- An advanced solution that reflects DataEndure’s four decades of experience in securing distributed environments.
- A committed partner dedicated to continuous improvement and successful business outcomes.
If you’re ready to take the first step toward a more secure future, we make it easy. We offer a complimentary Security Health Check to check key areas of vulnerability.