Chief Marketing Officer
In the realm of cybersecurity, the adage “lightning never strikes the same place twice” doesn’t apply. Organizations that have suffered one cyberattack are commonly targeted again, regardless of company size or industry.
Ransomware by the Numbers
Why Do Attackers Repeatedly Target the Same Company?
The first cyberattack yields detailed insights into a company’s security architecture and response protocols. This intel becomes invaluable for orchestrating subsequent attacks that are often more tailored and potentially more damaging.
The longer attackers linger within a network, and the more lateral movement they are allowed, the more entrenched they become, making them exceedingly difficult to eradicate completely. This persistence not only allows them to execute the initial attack more effectively but also lays the groundwork for future breaches.
Moreover, if the initial response to a breach is inadequate, it signals to the broader cybercriminal community that the organization remains vulnerable.
Adversaries Exploit Remaining Gaps Aggressively
Whether it’s insufficient updates to security measures, poor incident response, or simply the lucrative nature of the stolen data, all these factors can contribute to unwanted attention from cybercriminals.
The recent ransomware attack on Change Healthcare serves as a prime example. After suffering an initial attack by ALPHV/BlackCat, the company was quickly hit again by a second criminal group, RansomHub.
How to Break the Breach Cycle
To prevent recurrent breaches, organizations need to adopt a multifaceted approach to cybersecurity.
Proactive Measures to Take Post-Breach
- Thorough Incident Analysis: After a breach, conduct a detailed incident analysis to understand how the breach occurred and identify all affected systems and data.
- Enhance Detection and Response: Improve your threat detection and response across all threat vectors and update your incident response plan.
- Strengthen Access Controls: Reinforce access control measures. Multi-factor authentication, strict access policies, and adopting the principle of least privilege (also known as zero trust) can all help reduce the risk of a data breach.
- Ongoing Penetration Testing: Continuously test your security controls to look for chinks in your armor. An annual pen test isn’t enough in today’s threat landscape.
- 24×7 Security Operations Center (SOC): Ensure you have human experts monitoring for suspicious activities, actively threat hunting, and ready to respond swiftly.
- Employee Training: Keep employees current on social engineering techniques used by adversaries.
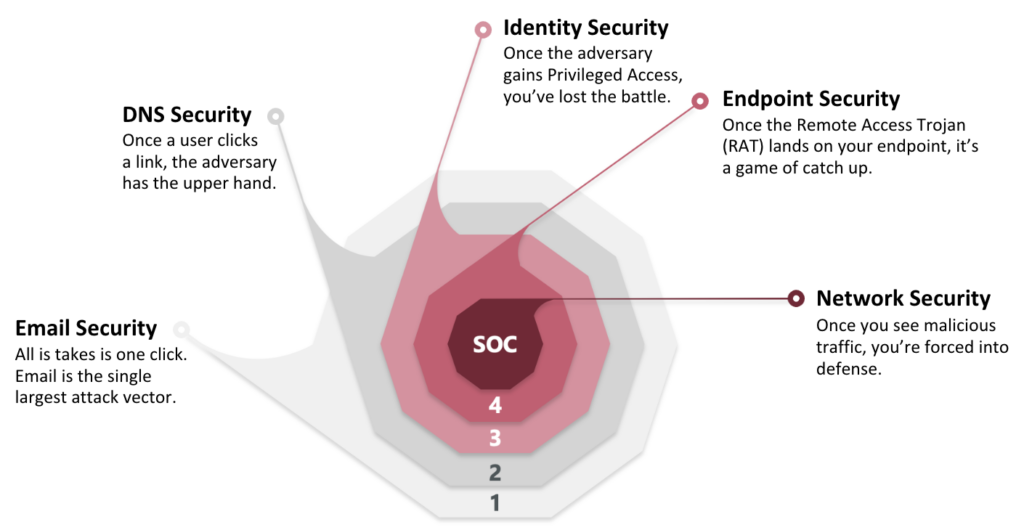
Why a Layered Defense is Vital
A cohesive, comprehensive defense is needed. Deploying multiple, specialized tools at each security layer provides a response tactic tuned for each type of attack.
Moving Forward with Resilience
Before an adversary strikes, companies must be prepared across all fronts to protect their business operations. This includes resiliency planning—updating your incident response plan, testing that plan, and fortifying your network and devices to make every attack surface as inhospitable as possible.
When an attack does occur, the primary business goal is to have a swift response, contain the damage, and prevent it from spreading. By implementing a robust cybersecurity framework and learning from past incidents, companies can greatly reduce their chances of falling victim to recurrent cyberattacks.
Post-breach, it’s crucial to conduct a root cause analysis to not only repair the immediate damage but also to identify and mitigate any backdoors left by attackers.
You Don’t Have to Face Threats Alone
In the world of cybersecurity, staying still means falling behind. Most companies want (and need) to do cybersecurity well, but given the complexity and pace of change, they simply don’t know where to start.
DataEndure has been around for four decades, and security has been foundational to who we are since day one. This experience informs how we build, manage, and evolve our security services.
We can work with you to strengthen your security posture in manageable, incremental steps, so you don’t become a statistic. Schedule a call today and move forward with resilience.