Chief Technology Officer/CISO
Excerpts from NorCal CyberSecurity Summit on September 5, 2018; session presented by Shahin Pirooz, CTO/CISO of DataEndure. You can watch the full presentation here.
More and more organizations and agencies are getting attacked on a daily basis, with newer threat vectors emerging faster than ever and even new business models developing to take advantage of the extremely lucrative cybercrime market. The city of Atlanta serves as a recent example (and warning) of the far-reaching implications a breach can have in a community across many services.
How do we, as IT leaders, meet heightened expectations to identify and respond – protecting the environment in a scenario of rising attacks but no rise in corresponding budget to be able to support, block and prevent those attacks?
The Squeeze is on:
There’s a 28% chance that if you’ve been breached, you will get breached again. And the average cost of that breach, according to Ponemon Institute, is about $3.6 million. By 2021, we’re expecting that the financial damages associated with cyber-attacks are going to be at $6 trillion.
Furthermore, it’s easier than ever before for someone to initiate an attack. Ransomware is the biggest movement right now. We are starting to see a global trend where large-scale ransomware organizations have created a SaaS model of their ransomware tools – inviting broader and deeper participation and lowering the bar of “entry” for perpetrators.
The Internal Challenge:
Ponemon Institute research reveals the average time to detect a breach is 201 days (or more than half a year). What’s contributing to this?
There are many tools, all making a lot of noise. For those who have a SIEM, 42% of the alerts that are popping up are being ignored. Who determines what is a priority to remediate? With most organizations struggling with resource constraints (in fact, 24% of organizations state this as a major concern). With exponentially more alerts and fewer resources to monitor, investigate and remediate, this creates a perfect storm. When we look more specifically at state and local data, the message is even more clear:
- 47% of local governments surveyed report being attacked daily (27% say hourly or more, and an additional 20% say at least once a day)
- 46% need more skilled information security professionals.
When asked “what keeps you up at night?” the risk and vulnerability of unsecured assets tops the list for almost half of government officials; with the same percentage rating the need for more skilled and knowledgeable infosec professionals as critical to fortifying their security posture.
Takeaway: This is a tools and talent challenge. Striking the right balance depends on the availability and expertise of the other. Tools and not enough skilled people? A waste. People with limited or no tools? Makes securing the environment a near impossibility.
Chicken or Egg?
The terms and concepts of security and compliance are often used interchangeably; this is at an organization’s peril. Security is the state of being free from danger. Compliance, on the other hand, is the act of doing what you’re supposed to do – providing a baseline or minimum bar you are expected to meet. It is not a focus on one or the other, but the complimentary forces working together, that will provide the most robust security posture.
Takeaway: Armed with compliance and security insight, you can perform a gap analysis, map it to where you are and where you need to go, then determine what else is needed to better protect the organization. Clearly, in order to proceed – you need to determine where you are today.
The Security Landscape:
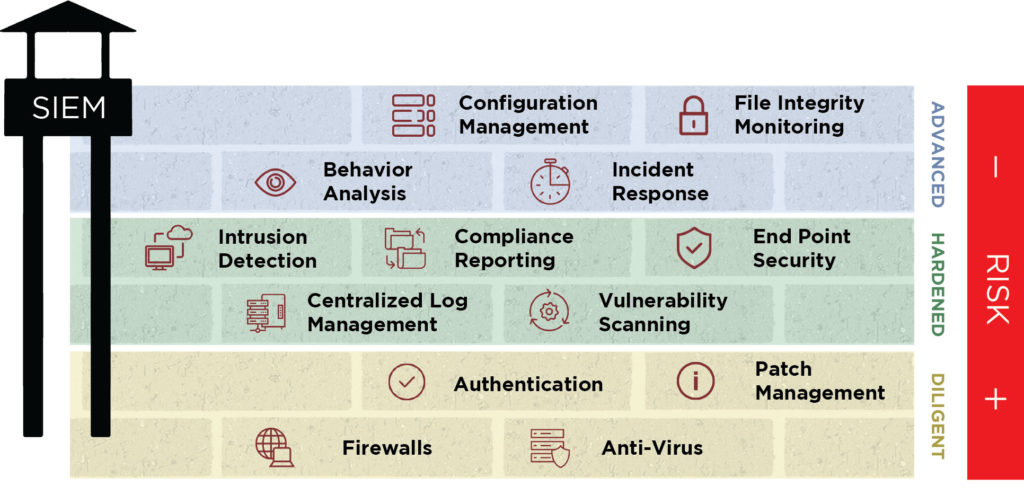
Given today’s threat environment, organizations, at a minimum, should be implementing the basics: anti-virus, firewalls, patch management and authentication.
For those who have sought to harden their environment with more advanced solutions, it certainly gives a boost to their security posture, however, it can also create a sense of having all of the right things in place. Unfortunately, the bad guys have moved beyond this in sophistication and technology.
Only at the advanced (top) level, are organizations able to achieve a solid incident response process. Behavioral analysis will help determine if something is doing what it’s not supposed to do and be able to catch it. File integrity monitoring provides insight into what’s going on with the files in your environment. And finally, configuration management, allowing you to have control of your configuration to know if something has changed without your knowledge, exposing you to risk.
Takeaway: Two key challenges to how organizations approach security controls: First, with users everywhere, there is no edge anymore. And second, companies are doing things like implementing SIEMs but not allocating resources to sit in front of those SIEMs. The tool doesn’t deliver value (or risk mitigation) unless it has the appropriate resource commitment to leverage it.
First things first
It doesn’t have to be complicated or costly to baseline where your organization is today. To understand where you are on the security model discussed above, two activities that can provide clarity and detail are a compliance health check and vulnerability health check.
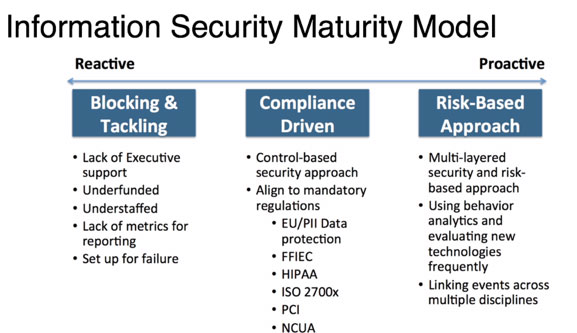
Once you have determined where you are, you are then able to map the “actual” to the “theoretical” (where you want to go). An Information Security Maturity Model can be helpful in this exercise. In most scenarios the goal of an organization is to move from a Reactive position (blocking and tackling) to a Proactive, risk-based approach.
Takeaway: Every organization has a different risk profile and tolerance. That said, with the intensity of cyberthreats that exist today, any organization where data integrity and information security is an integral part of their business, should consider a Defense-in-Depth strategy. An organization needs to be able to:
- protect your environment,
- detect when something happens,
- recover after that something happens, and leverage encryption so that if something happens that data is garbage to whoever took it,
- analyze and manage the environment
The Resource Question
Having a strong digital defense requires a strong offense. In many situations, security resources are constrained. One approach is to look at a managed security service provider that offers a Security Operations Center as-a-Service that can serve as an extension of your team. The economics are compelling; consuming SOC as-a-Service costs a fraction of what it would take to build out your own SOC and staff it 24/7.
Your Checklist
When you evaluate platforms or third-party providers, the table stakes for any managed security service provider should be their ability to correlate data across all your different log sources, identify and prioritize threats and provide remediation recommendations. But this is just the beginning.
What Else Matters?
- Make sure the provider isn’t just a security player, or a compliance expert or an auditor. As we’ve discussed – a provider needs to demonstrate capabilities that encompass your security AND compliance needs.
- If you’ve got a good partner with a proper SOC, they’re going to be doing the “analyze” and the “manage” side. They will also use what they are learning to offer insight on any gaps in the environment they are seeing on a regular basis through vulnerability tests and specify the areas that require attention from a risk approach.
- Work with a provider whose pricing rewards threat reduction. If you are being charged per TB of data or events/second, the provider makes more money the more issues you have, with no incentive to reduce threats. Look for someone who charges a predictable fee, where both organizations benefit when threats are reduced in your environment.