Chief Technology Officer/CISO
Highlights from DataEndure’s recent Keynote and Cocktails event featuring Shahin Pirooz, CTO/CISO, DataEndure and Jeff Gallager, VP Events, IDC
Companies are increasingly dependent on technology to drive innovation and their digital transformation strategies. With people and data everywhere the simple act of being connected – whether it’s through mobile devices, IoT, or other areas – creates risk. And where there is risk, there is opportunity for attack.
When we say your company is under attack, the main targets are people in your company ranging from the CEO and CFO all the way down to the person that works in the mailroom. Email is the number one inbound target with phishing attacks becoming so sophisticated that even the most diligent employees can be deceived. All it takes is for someone to open an email and click the wrong attachment by accident. The majority of ransomware phishing attacks start with a simple website click that downloads the Trojan that’s getting in.
No One is Immune
Many organizations say “Nobody is going to target us. We’re not the focus. They’re not going to come after us.” The fact of the matter is 60 percent of the organizations we’ve researched said they’ve had, on average, at least one attack in the last 12 months. When you take it to the enterprise, it actually moves up to 70 percent.
A couple more data points:
- The first half of last year there were 81.5 million ransomware attacks. That’s 229% greater than the year before.
- Damage cost is predicted to be 57 times greater in 2021 versus 2015. When you translate damage in terms of dollars, by 2021, it’s estimated to be $20 billion.
The Importance of Digital Resiliency
Resiliency is really the most important, most valuable property of any organization. And developing resiliency is more essential than ever before due to new cyberattack strategies and how quickly they are escalating and changing.
At its core, resiliency is about being prepared. It’s about being able to respond. It’s having the ability to survive and thrive in an attack. That attack may be cyber. But that attack can also be weather, or a system failure…it could be anything.
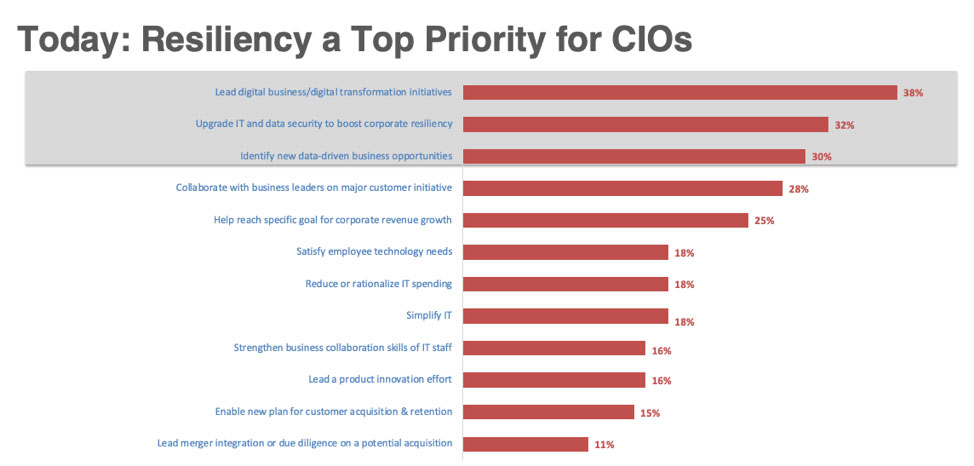
In fact, building out corporate resiliency ranks #2 in terms of priorities that CEOs are pushing down to CIOs.
Source: State of the CIO, 2019
It is critical to have leadership involved in your resiliency strategy. And the strategy needs to include governance, risk and compliance to make sure you’re doing what you need to do for whatever regulatory bodies that are controlling you. Other key factors include how you store your data, secure your data, protect your data and facilitate the movement of your data. Finally, critical to transformation initiatives is the ability to collect insights from your data to make business decisions. All of these are interrelated and can’t be looked at (or managed) in a silo.
What can be done?
- Use basic, common sense. For example, don’t give IT administrative privileges to end-users.
- Implement a multi-factor authentication system.
- Don’t rely on cyber-insurance alone, and if you have it, make sure you have a clear understanding of the fine print as many claims go unpaid.
- Many are comfortable because they have firewalls, they have anti-virus, they have good IT people. These tools aren’t enough and can often lead to a false sense of security.
We’re seeing organizations starting to realize that while it’s important to defensively block attacks, it is as important to quickly recover when something gets through. This is where the “survive and thrive” comes into play.
Organizations need to recover their data in the midst of an attack quickly and get back to business within minutes, not days or months. And even if it was encrypted, recovering without having to pay out a ransom.
There isn’t an easy solution; but there is a way to strengthen your defense while going on offense.
The ability to recover quickly requires close attention to how information is managed – both the protection and storage of data – tied with security.
If you could build it yourself, wouldn’t you design a security solution that not only monitored and alerted you on what has happened in your network, but was able to work harder for you to assess, analyze and report on the overall health of your security tools, configurations, ability to perform and the like? We agree.
As a response to our clients and their need to take a more proactive cybersecurity stance, DataEndure is now offering Digital Defense SOC-as-a-Service (SOCaaS). This managed security service is an ideal solution for companies to augment their own security capabilities. Serving as an invested security advocate with the latest technology and deep expertise, we can help your organization become less reactive and more resilient in an ever-evolving threat landscape—without draining IT resources and budget.
To learn more about how DataEndure’s SOC-as-a-Service (SOCaaS) can protect your organization, contact us today.