In our previous blog, we looked at the unprecedented cybersecurity challenges of 2020. In today’s blog, we look at how DataEndure’s approach to a fully-managed security solution helps put organizations on offense and take the critical time advantage away from cyberadversaries.
While adversaries have quickly evolved, many tools have not.
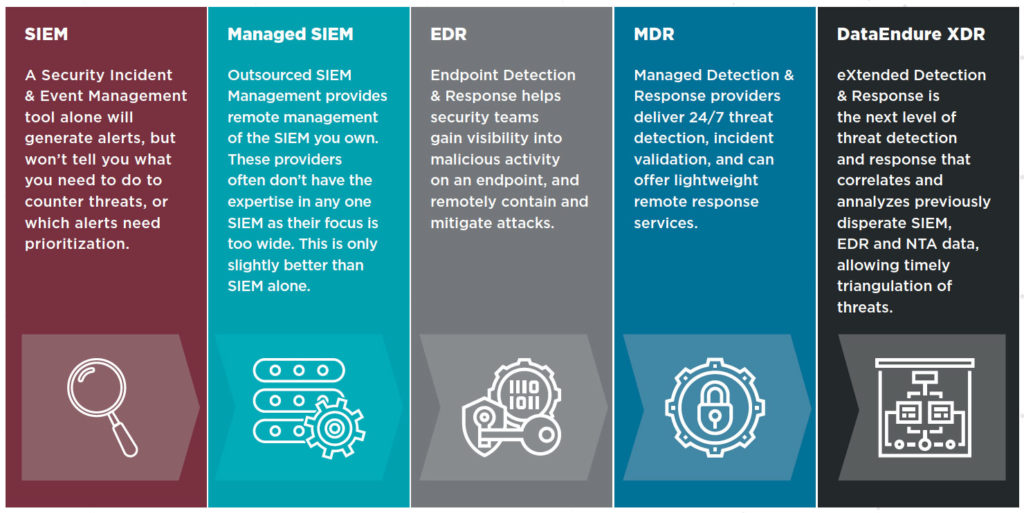
A fully-managed security solution with a robust and complete security stack can bridge the gap between your organization’s time and resource demands, providing the required expertise to stand up a multilayered security program that detects threat actors wherever they emerge, in real time. Yet without industry-standard language in place, many providers use terminology that suggests their solutions are far more robust than they are in practice. For example, many solution providers utilize the term “XDR” (eXtended Detection & Response) to describe services that in reality provide only EDR (endpoint detection and response); the same holds true for MDR offerings on the market – it falls upon the buyer to have a clear understanding of what the provider does, and if the service maps to their needs.
With such a dynamic market, it is helpful to understand how security services have grown and changed, and how the scope of the solution provided differs between tiers of service:
Enlisting a team with decades of cybersecurity expertise helps you take back your time.
The goal for any organization is to put time back on your side by strengthening and accelerating your ability to respond to an everchanging threat landscape. DataEndure works by your side and on your behalf and can offer you a fully realized security program, for a fraction of the time and expense of going it alone. DataEndure utilizes a Modern Defense-in-Depth approach: a security construct emphasizing a multi-layered approach to digital defense that supports and secures today’s distributed workforce and ever-expanding edge.
It’s considered the gold standard for cybersecurity, and with good reason: with so many tools and techniques integrated into a single program, multiple lines of defense can be deployed to detect and respond to even the most sophisticated bad actors, inside or outside of your organization, before they can do any damage. By enlisting experts, you gain your time back to focus on your core business. A telemetry-based approach to prioritizing threat responses can be realized faster than developing an in-house solution, giving you increased time to value. Finally, by enlisting managed cybersecurity experts, you take away one of the most valuable tools a cybercriminal has to hurt you, the time it takes to discover and remediate an attack in progress (dwell time).
The end result: a robust managed security solution that helps you turn time to your advantage.
Stay tuned for next month when we will wrap our series with a look at the specific technologies and methodologies that help accelerate threat detection and improve investigation and response times. In the meantime, we are offering our complimentary Security Health Check to help you evaluate your current security posture. This health check will give you the insight and opportunity to strengthen your defenses before a potentially crippling attack occurs.