Chief Marketing Officer
The concept of “The Enemy at the Gates” has been used to describe the security threats facing organizations around the world. The problem with this analogy is that the threats are no longer limited to just the “gates”. Today’s borders are fluid because our endpoints live everywhere. In the traditional model, we focused on (and were limited to) protecting what’s inside our offices. With people working from anywhere and data everywhere, we can no longer depend on a single gate of firewalls to protect our entire environment. Let’s look back at a medieval concept, and see how we can apply it to the modern threats we face today, creating a layered defense able to fortify the modern day castle.
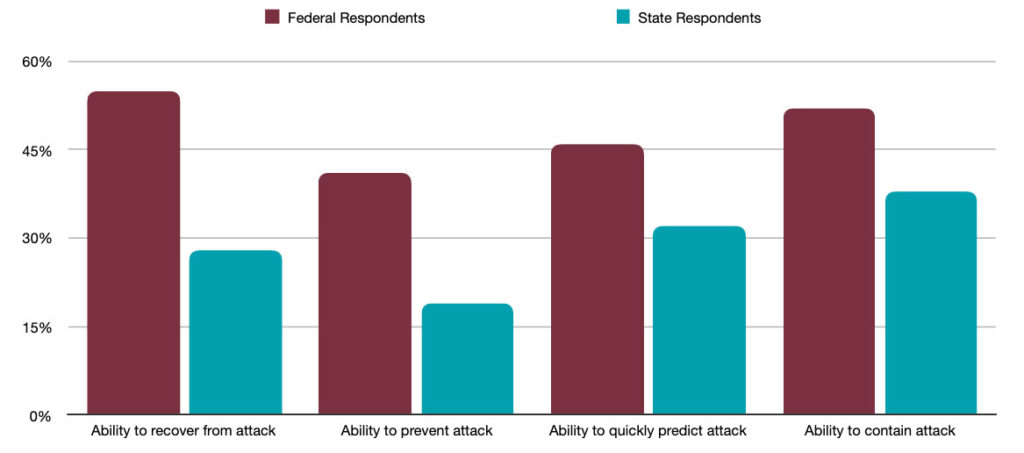
According to Ponemon’s The State of Cybersecurity in Local, State and Federal Government, in the last ten years, there have been over 10,000 breaches in the United States resulting in around $1.6 trillion in losses. Sadly, California has been hit more than anybody else. In addition, the report highlights how ill prepared states are when it comes to preventing and recovering from attack.
In the following chart, we can see the difference in preparedness between federal and state respondents in four key areas:
So how do state and local governments improve their preparedness in a world where attacks are coming from multiple directions and locations? We believe the answer is what we call Defense in Depth.
Defense in Depth takes into account your information security: how you manage it and how you protect it. But it also applies to your infrastructure: everything from your data centers to your literal end points – the PCs and Macs and mobile devices that are out in the field. Organizations need to account for both to understand how best to apply security broadly.
Defense in Depth also incorporates an offensive and defensive approach. Not only should you be able to recover quickly from a failure, but also have the tools, capabilities and visibility to know an attack is happening early and prevent it, block it or stop it before it takes hold and causes damage.
In medieval castles, perimeters would provide a first layer of defense against an enemy entering through the gates. Next would be a moat and a drawbridge. Then archers on the piers shooting oncoming attackers. Finally, there would be guards in the towers monitoring long distances for oncoming enemies.

Even with all of these tools in place, there is no guarantee that you can prevent adversaries from coming inside your network. So how do you respond? By building incident response plans, tools and systems. And to ensure you know when something is happening zero-day in your network, a User Behavior Analysis is critical.
It is important to note that a SIEM without a SOC is like a guard tower without a guard. Being able to have people who are looking constantly at your environment, monitoring events, looking for threats and investigating those threats is the key to understanding what is happening in your environment and reacting before something happens.
This multi-layer “in depth” approach protects every layer of your platform and also proactively monitors it. If you have all the right tools in place and you’re not monitoring and interpreting the data, you really don’t have visibility into threats that are happening.
Unfortunately, the number of tools that are out there is massive, and many organizations find it difficult to pick the right tools to fit in each of those categories and address the problems in their environment.
Possessing years of real-world experience with these products across many companies, DataEndure helps our customers understand what’s out there, what works and what doesn’t. Other organizations have made significant investment in tools already; yet still lack confidence in their security posture. A security controls validation can provide critical insight, determining if the tools are doing what they are supposed to.
Are your defense systems robust enough to withstand today’s threats? Sign-up for our free Security Health Check and get answers within 14 days.