
Chief Marketing Officer
In a rising tide of sophisticated cyberattacks across all sectors, in order to survive and thrive, organizations must implement advanced threat detection and response measures. The goal is to reduce the amount of time an adversary goes undetected in your environment, known as dwell time.
Endpoint Detection and Response (EDR) has received a lot of attention, as it should. Endpoints are a critical part of a layered defense strategy. That said, endpoints are only 1 out of 6 common attack vectors, so an endpoint-only defense leaves companies very exposed.
XDR can deliver a layered defense.
What’s needed to up-level your defense is a comprehensive approach that covers all threat vectors—extended detection and response (XDR). The concept behind the “X” in XDR is to secure your environment across all threat vectors:
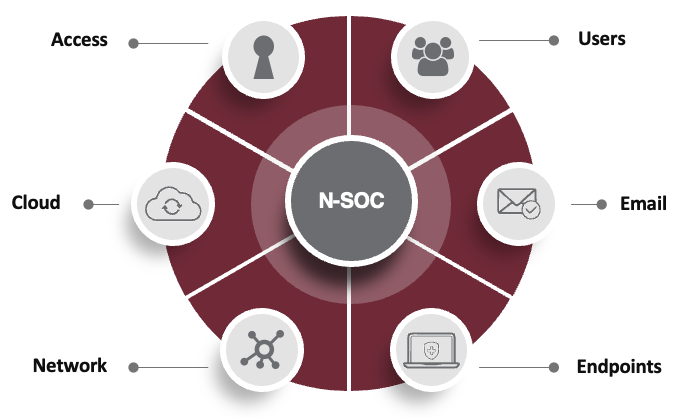
Defending against today’s evolving threats requires more than layered security. XDR combines security measures to provide a comprehensive layered defense—by deploying multiple, specialized tools at each security layer, organizations have a response tactic tuned for each type of attack.
The thing is, not all XDR solutions are created equal.
A lot of security vendors have jumped on the bandwagon, and there are two groups—those who deliver on XDR’s promise and those who don’t. To help you evaluate the many options out there, here are some key factors to consider.
Response is where the true power of XDR lies.
While many cybersecurity players collect logs and monitor various data sources, there’s a key component missing in many offerings: the response functionality. Sure, they might excel in detecting suspicious activities, but what happens next?
What sets a complete XDR solution apart is its ability to respond effectively across multiple layers of an organization’s environment.
It’s not just about stopping threats at the endpoint; XDR takes a holistic approach to response. This includes email response, DNS response, network detection and response (NDR), identity protection, and even access-level response through Zero Trust Network Access (ZTNA). Each layer adds a new dimension to the defense, creating a multi-faceted shield against cyber threats.
Email and DNS are critical battlegrounds.
Email and DNS are two critical battlegrounds in the fight against cyber threats. A staggering 93% of attacks start with email, making it a prime target for malicious actors. Similarly, 80% of malware requires DNS for command and control.
Yet, surprisingly, most “XDR” solutions leave these critical gaps open.
The more telemetry, the better.
The collection of data from various sources forms the foundation of XDR’s effectiveness. Without monitoring telemetry from all relevant sources, a security solution is incomplete. This is where XDR shines, as it aggregates data from endpoints, DNS, networks, and more to “triangulate” threats.
The more X’s you have in your XDR solution, the more extensive your data collection. This allows for early detection and swift response, significantly reducing the dwell time of threats within an organization’s environment.
Active threat hunting requires AI + human expertise.
A fully baked solution isn’t just about data collection; it’s about what happens next—real-time monitoring and analysis. While many solutions rely on automated rules and alarms, this misses the critical human factor. Without a dedicated security operations team scrutinizing telemetry around the clock, organizations are missing a crucial aspect of security.
Combining the power of AI and human expertise ensures that alarms are investigated thoroughly, distinguishing between false positives and genuine threats. Early detection and rapid response are key factors in minimizing the potential damage caused by cyberattacks and drastically reduces the dwell time of threats.
While many solutions might only kick into action after an attack has been executed, a fully-fledged XDR should be capable of identifying and countering threats in their early stages, preventing potentially catastrophic damage.
Staying ahead of threats requires a complete solution.
Most companies want (and need) to do cybersecurity well, but given the complexity and pace of change, simply don’t know where to start or don’t have the resources to fully assess/address their needs.
The best place to start is to understand your current security posture—what have you already invested in, is it working, and where are critical gaps? From this baseline, you can create a roadmap that prioritizes the gaps that need to be addressed immediately and what can wait. If you’d like help creating your security roadmap, we’re here to help.