Chief Marketing Officer
With 3,000 cybersecurity tools on the market, and many threat detection and response tools that sound the same, it can be difficult to discern what’s best for your business. Depending on the research report, enterprises deploy between 40-70 security tools.
So, let’s take a look at your options (in today’s threat landscape, doing nothing is no longer an option):
1. Do it yourself – run multiple POCs, purchase, install, integrate, manage, staff, and wash/rinse/repeat 40 to 70 times. You’ll need to figure out a way to make sense of the alert chaos because the average mid-size business gets over a billion alerts a year (not a typo). You’ll need to build a process to identify and remediate issues across all the tools. And this is just a sampling of what an organization needs to do to have a mature security posture.
2. Buy a Swiss Army knife (or several) – find several core vendors who cobble disparate technologies together. The benefit is they’re all in one. The downside is they’re all in one. But, like a Swiss Army knife you’re paying for the all-in-one, not the best tools. But in security, the difference between good and best could cost you your business. And, bear in mind, the burden is still on you to integrate tools that don’t natively play well together. You’ll need to figure out how to get full visibility between all the tools and data the tools are providing–and you’ll need a team to oversee it all, continuously tune, and respond.
3. Find a managed security services provider (MSSP) – who has identified best in class, handles integrations and upgrades, staffed 24×7 to expertly monitor, identify, and remediate issues. It’s not on your shoulders to figure it all out.
What Are the Four Types of Threat Detection?
To protect your company from cyber threats, you might be tempted to just buy a few threat detection and response tools and check off the box. But that doesn’t go far enough—you need a multi-layered approach and a security operations center that can keep eyes on your tech stack at all times to truly be protected.
Before we jump into discussing how to develop the right mindset for threat detection and response, let’s first take a closer look at the different types of threat detection:
- Threat Intelligence: Use data analysis based on past events to detect similar ones in the present that could indicate an oncoming attack. With threat intelligence, you can also identify vulnerabilities in your systems that need to be addressed so attackers stop exploiting the same weaknesses.
- Attacker and User Behavior Analytics: Identify unusual user and network behavior that may point to potential threats. Don’t wait around for these threats to turn into attacks. Take action before an attack can occur.
- Intruder Traps: Draw intruders to bait, or honeypots, within your systems and receive alerts once an attacker takes the bait. You use this method to draw out intruders lurking in the shadows of your cyber environment.
- Threat Hunts: Use a security operations center (SOC) with trained experts who will actively track down intruders 24/7/365. The SOC will use a mix of methods and tools for a robust offense and defense against attackers.
Your cybersecurity arsenal must be just as diverse as the attacks your company faces. That’s why you need to implement several different methods of threat detection in your cyber security strategy. Using a mix of tools, methods, and human eyes takes the power from intruders and puts it back in your own hands.
What Are Threat Detection Tools?
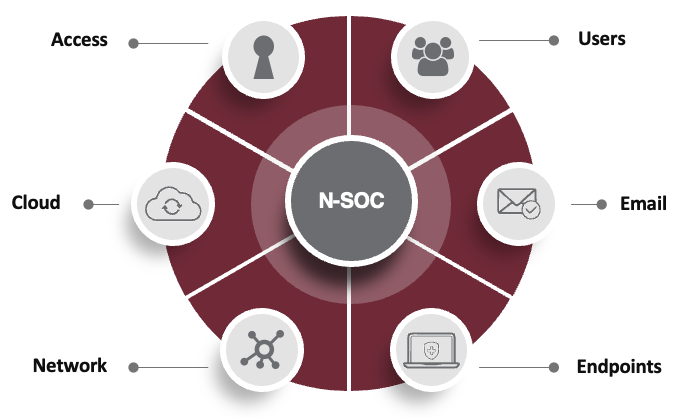
Threat detection tools are used to identify and respond to threats across your organization. Some tools can automate responses while others send alerts to your IT team so they can then prioritize and respond. There are 6 key critical attack vectors that demand protection; and, within each vector, there are specialized tools and techniques to combat the type of attack coming at you.
For example, endpoint detection and response (EDR) tools defend your endpoints—any device that connects to your network. Security information and event management (SIEM) provides monitoring and analysis of real-time events as well as tracking and logging of security data to help you recognize potential security threats and vulnerabilities before they have a chance to disrupt business operations.
However, extended detection and response (XDR) moves beyond a point solution to provide comprehensive, cross-vector protection. Your tech stack has many layers, and your cybersecurity should work the same way. With XDR, it can.
XDR works to minimize the number of attackers making their way through your defenses. Every layer is purpose-built to remove threats with the right response tactic. At each layer, you’re defanging that threat attempt with the appropriate weapon.
How Do You Create a Threat Detection System?
To create a threat detection system, you need a layered strategy that can keep pace with a dynamic threat landscape. Of note, 58% of executives aren’t confident that their current strategy is protecting the business from cyber threats. So, before you start investing in threat detection software, make sure you’ve done your homework:
1. Analyze your tech environment. Understand what users and endpoints are connected to your systems; where your critical information resides; who needs access to it; what regulatory requirements you need to comply with; assess your vulnerabilities across all vectors; and, prioritize what needs remediation first.
2. Establish a baseline of what normal behavior looks like. This way suspicious behavior stands out as something that needs inspection. The faster you find nefarious behavior, the better.
3. Create an attack response plan. It’s not a matter of if, it’s when. The attack response plan is everything you need to do to put the process and people in place once you have an indication of compromise. You need a swift response to mitigate the damage and restore business operations as quickly as possible.
4. Don’t make the same mistake twice. 80% of ransomware victims are breached again. Just because your business operations are restored doesn’t mean you’re not still vulnerable–ensure you’ve closed your security gaps so you don’t give criminals repeat business.
5. Make sure experts have your back. Whether you build a team or leverage a managed security services provider (MSSP), make sure you’ve got the right people and the right expertise. Cybersecurity is a specialized skill and not one you can afford to underinvest in (the adversary is hoping you do).
Cybersecurity is not one-and-done, and you can’t have a set-and-forget mentality. Technology and cyberattacks are constantly changing, and your cybersecurity solutions must be able to adapt.
DataEndure: Threat Detection and Response Solutions That Just Work.
The best indicator that your threat detection and response solution is working: dwell time. At DataEndure, it’s our priority to minimize the time an adversary has to do damage in your environment. With an average dwell time of just 6 minutes (compared to the industry standard of 6 months), we put the time advantage back on our customers’ side.
For four decades, digital resilience has defined our business and delivered successful outcomes to our clients. If any or all of these goals map to your security objectives, let’s talk.
- Accelerate your security maturity (30-90 days)
- Lower costs (50% less than doing it yourself)
- Attain an evergreen security solution
- Gain 24x7x365 experts to monitor, alert, remediate, and restore
- Reduce dwell time to minutes vs months