Chief Technology Officer/CISO
Original blog posted by DataEndure CTO/CISO, Shahin Pirooz on linkedin.com.
DataEndure has traditionally highlighted a security “trifecta” of DNS security, endpoint security, and our SOC-as-a-Service as a way for organizations to fortify their security posture, there has been a fourth category that has jettisoned itself onto the stage, earning a fourth designation. COVID-19 and the rapid movement of employees to remote locations has introduced an expanded threat surface and new security challenges. Consequently, anti-phishing and spear-phishing have intensified in a way no one could have imagined, accelerating malware exposure and distribution through vulnerable employees.
A security “FourFecta” provides a framework to help you keep your organization secure during this challenging time, and beyond. While there is no silver bullet that can completely secure an organization, a modern layered defense in depth approach puts you on a solid defense and provides prescriptive offense against cyber adversaries. In this article, I offer some background and reasoning for each layer of DataEndure’s “FourFecta.”
1. Anti-phishing/spear-phishing Prevention
Phishing has always presented the largest attack surface for any security team and has increased dramatically since the beginning of the COVID-19 crisis – by some reports, 667% since February. Social engineering and phishing campaigns are a primary method of malware distribution, and there is an abundance of bad actors taking advantage of people’s anxiety and “need for information.” Due to the increased use of personal devices and work from home, attackers are targeting the weakest link in the chain, which is often individuals and their personal systems on insecure home networks.
Knowing that even the most aware human will make mistakes, we recommend an Advanced Email Security and Defense program designed to stop phishing and spear-phishing attempts in addition to actual malware before it ever gets to the end user. Many organizations have phishing awareness and training platforms in place; while this is a great start, these platforms rely on your end users as the first line of defense. Given the efficacy (and creativity) of phishing attacks, relying on user training and discretion is not enough. You must prevent the phishing attempt from even getting to your end users in the first place. This first line of defense is crucial, but it doesn’t stop here.
2. DNS Defense
DNS is the lifeline to the internet. Without it, we would be lost trying to remember all the IP addresses of sites we want to visit – and fail miserably. While the internet would not be what it is today without DNS, we should not have blind faith in it. We don’t often inspect where a DNS server is sending us, and savvy adversaries take advantage of this by creating sites that look and sound like popular and well-known sites to try and hijack our credentials.
When a phishing attack is successful, and your end user clicks on a link that takes them to one of these malicious sites, the damage is done. Malware begins downloading in the background, and the user’s credentials are harvested. Why do we care if the user’s target.com password is compromised? Most people don’t use a password manager, and often use their work email and the same password for many of the sites they visit (including their corporate account). So, if an adversary has their Target credentials, they likely have their Active Directory password as well.
For these reasons and many more, we need to help our users be successful by blocking access to known malicious sites or URLs. A good Defensive DNS solution can prevent all of the above. While a web proxy is helpful for anyone in the office, it doesn’t help the growing number of individuals working from home, Starbucks, or a client site; therefore, a distributed cloud-based DNS Defense is key. These factors make DNS Defense the second line of defense, but we are only halfway there.
3. Endpoint Security
Next-generation endpoint security works in conjunction with the Advanced Phishing Protection and DNS Defense, adding yet another crucial layer of defense against threats that may get past the previous layers.
Traditional endpoint security solutions are no match for today’s adversaries because they rely on file and malware definitions or signatures which can’t protect against zero-day threats. What we are classifying as next-gen endpoint security requires that the solution is behavioral-based and doesn’t rely on signatures. Further, it should include machine/deep learning in order to identify threats based on their actions rather than what is known about them historically, because adversaries constantly change malware and malware behavior to avoid detection. The best solutions leverage industry definitions of the techniques, tactics, and procedures (TTP) adversaries use – the ATT&CK Matrix curated by MITRE is the de facto standard.
If you already have the first two lines of defense, why does the type of endpoint security matter? As an example, if a phishing attempt bypassed your user training and defense solution, and the new malicious site is not yet in any threat databases. There is no intelligence to identify it as bad and block it, and this is why the third level of defense is critical. The behavioral-based endpoint security solution will stop and block the threat based on what it is doing on that endpoint, not relying on a signature match.
4. SOC-as-a-Service
The final line of defense and protection in DataEndure’s “FourFecta” is our SOCaaS (SOC-as-a-Service). With today’s rapid pace of change, the importance of having a trusted ally on the front line becomes a necessity. Having a SOCaaS working for you means that our security experts are providing continuous monitoring and testing to ensure the efficacy of your security controls and finding threat actors in your environment before they gain a foothold.
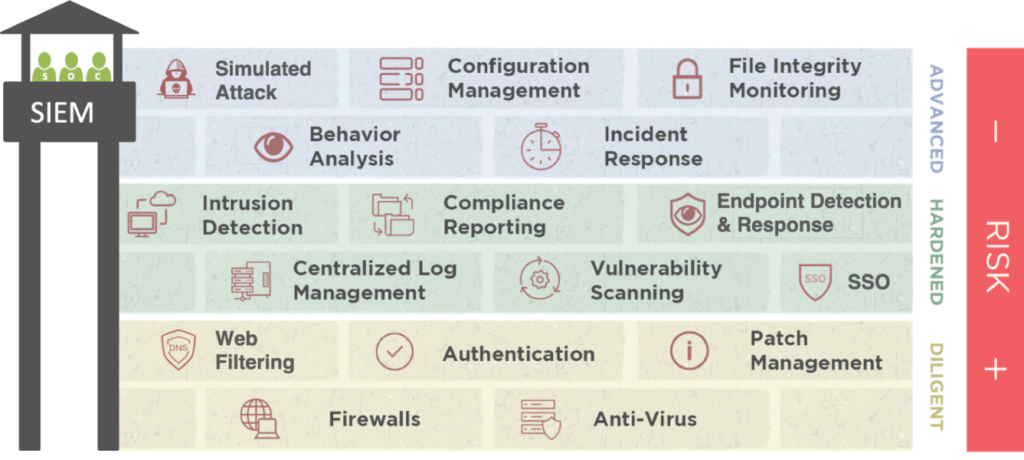
We have had clients who had Anti-phishing, DNS security, and endpoint security solutions in place, yet they had been tweaked in such a way over time (“configuration drift”), creating exposures they weren’t aware of. The traditional thinking of once per year penetration testing is not enough to find this configuration drifts as they happen, which creates exposure and increases risk. Adding a SIEM to this mix doesn’t solve the problem – a SIEM without a SOC is like a guard tower without the guards. Having a robust SOCaaS provides the defense they need to identify and inform them of security gaps, keeping them ahead of the bad guys, giving the good guys the advantage.
Others had previously invested in a SEIM and a SOC, believing that was ample protection. However, a SEIM alone is never enough, as it is a reactive tool that processes log data to find indications of compromise (IOC). The challenge is that those bad actors, at least skilled ones, don’t leave a trace behind in the logs, and a SIEM can’t process what isn’t there. Even if you have highly skilled security staff (internal or external) monitoring your SIEM, it is not enough. At this point, the level of resources and time you’ve invested in your security program begins to parallel investments that are core to your business – and can start to become a distraction.
Our clients value that we do all the research, investment, and integration, so they don’t have to. It takes a combination of 11 security tools and products to round out our arsenal fully and, by extension, our clients’ security programs. Our SOCaaS offering includes SIEM, NTA, UEBA, Threat Intelligence, Continuous Vulnerability Assessment, and regular Security Controls Validation (Purple Team). And the icing on the cake? We are not only looking for IOCs and threat hunting, but we include continuous vulnerability management and simulated attacks (leveraging the ATT&CK Matrix TTP) to ensure that your preventive controls are doing what you expect them to. Without the simulated attacks, you don’t know the real impact of configuration drift on your security controls.
This layered approach may sound overwhelming, but it doesn’t have to be. As your organization responds to current and future challenges, DataEndure’s “FourFecta” strategy provides a robust approach to dealing with the ever-evolving threatscape. As a result, you can focus on what differentiates you against your competitors and impacts the bottom line.
Where to go next? DataEndure is extending a complimentary Security Health Check to help organizations ensure your security tools and controls are working and can detect threats and respond to incidents no matter where you are operating. You’ve got a lot to do. Let us help.