Now more than ever, cybersecurity is everyone’s business (Part 3 of 3)
In our previous blogs, we have been looking at how DataEndure’s approach to a fully-managed security solution helps put organizations on offense and take the critical time advantage away from cyber-adversaries. Today, we wrap our series with a look at the specific technologies and methodologies that help accelerate threat detection and improve investigation and response times.
The DataEndure X-Factor
DataEndure’s XDR-as-a-Service brings a practical and proactive approach to threat detection and response by integrating, correlating, and analyzing data across many security tools. With users and devices expanding outside the traditional edge – and farther from IT visibility and support, XDR allows for the timely identification of threats in your environment by triangulating multiple points of telemetry from many sources to find the bad actors, not just the indication of a compromise or risk.
Our Approach: A `Modern Layered Defense
Our goal is to ensure you have the best possible security posture available in the industry. Our approach combines many integrated technologies and methodologies which provide the critical telemetry to help accelerate threat detection and improve investigation and response times.
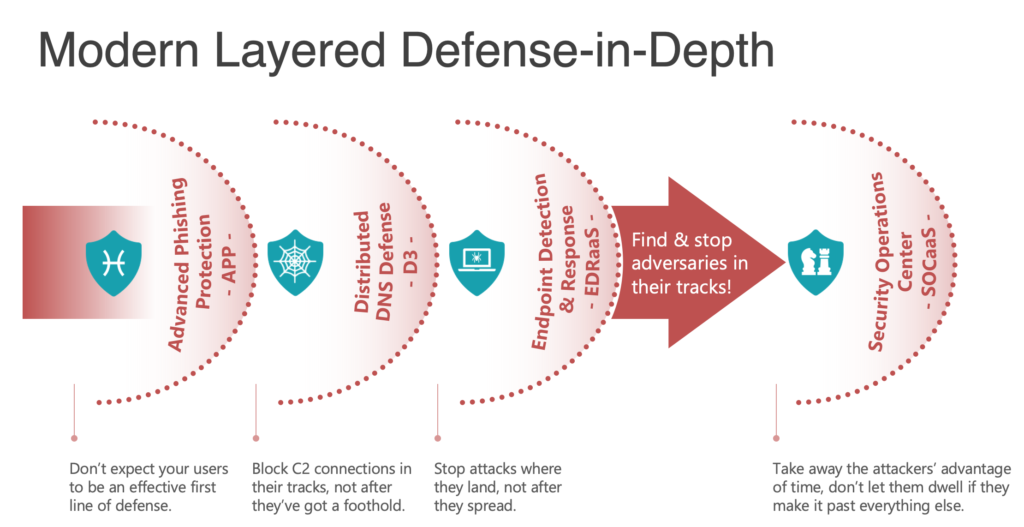
Layer 01.
Advanced Phishing Protection is the first line of defense. It’s a dangerous strategy to rely on security awareness training for your users as a solid first line of defense. With cyber-adversaries who are crafty and agile, you also have to protect users from themselves by preventing the phishing, impersonation and spoofing attempts from getting to them at all.
Layer 02
Distributed DNS Defense is your second line of defense. It’s not enough to prevent DDOS attacks, you must have threat intelligence to know where bad sites are and block them in case your first line of defense doesn’t work.
Layer 03
Endpoint Security is the third line of defense. Your endpoint security solution should not just be focused on file-based threats - the days of signatures and definitions are long gone. To prevent malicious execution, you must be able to monitor tactics, techniques and procedures executables are using, stop them in their tracks and roll back the damages.
Layer 04
Security Operations & Orchestration is the critical final layer of defense. Your SOC needs to include telemetry from all aspects of your environment, not just the endpoints and not just the network. While a SIEM is critical for full security log aggregation, correlation and management, it is not enough on its own.
For full visibility into the health of your security posture, it also must include User and Event Behavioral Analytics, Network Traffic Analysis, Host Intrusion Detection Service, Network Intrusion Detection Service, File Integrity Monitoring, Advanced and active threat intelligence, Continuous Vulnerability Assessment, Security Orchestration & Automated Response and running continuous simulated attacks (purple team activities) leveraging the MITRE ATT&CK Matrix TTPs. All of these sources of telemetry must be aggregated and correlated to enable rapid identification of indicators of compromise so that your security team can begin investigation of threats.
Help your security keep up with the speed of business.
DataEndure addresses your security and compliance challenges in a cost- and time effective manner, so that you can focus on growing your company without spending precious time thwarting potential threats. Serving as an invested security advocate with the latest technology and deep expertise, we can help your organization become less reactive and more resilient in an ever-evolving threat landscape, without draining IT resources and budget. Help your security keep up with the speed of business with DataEndure as your trusted partner.
We are offering our complimentary Security Health Check to help you evaluate your current security posture. This health check will give you the insight and opportunity to strengthen your defenses before a potentially crippling attack occurs.