Chief Marketing Officer
As workers and data become more distributed, bad actors are capitalizing on weak security points. In fact, Forbes reports that cyberattacks are nearly twice as frequent in 2023 as they were in 2022. Attacks are not only more frequent–they’re more costly. Verizon’s 2023 Data Breach Investigations Report reveals that the median cost to victims per ransomware incident more than doubled over the past two years to $26,000, with 95% of incidents resulting in a loss of between $1 and $2.25 million.
When the act of just doing business is growing riskier, how prepared are you?
- How can your team adopt a security-focused mindset?
- What can your business do to improve threat detection and response?
- Which cybersecurity threats and solutions are worth considering?
This blog will provide cybersecurity best practices for a business.
Do Small Businesses Need Cybersecurity?
Yes! Cybercriminals don’t discriminate based on company size. Attacks are increasing in frequency and cost across all industries and company sizes. Small businesses are often more vulnerable because they assume only big companies get targeted or the thought of putting robust security into practice is overwhelming. The task seems too big, too complicated, and too expensive; but, doing nothing is not an option:
- Small businesses are three times more likely to be targeted by cyberattacks than large companies (Forbes).
- Cyber attacks cost small businesses an average of $2.2 million per attack (LinkedIn).
- 60% of small businesses go out of business within six months after falling victim to a cyberattack (Forbes).
For a small business, a compelling option is to use a managed security services provider who does all the heavy lifting, staffing and offers services for a fraction of the cost of building it on their own. And best of all, they can leapfrog to security maturity in 30-90 days vs. months or years.
What Is the Most Important Aspect of Cybersecurity for Businesses?
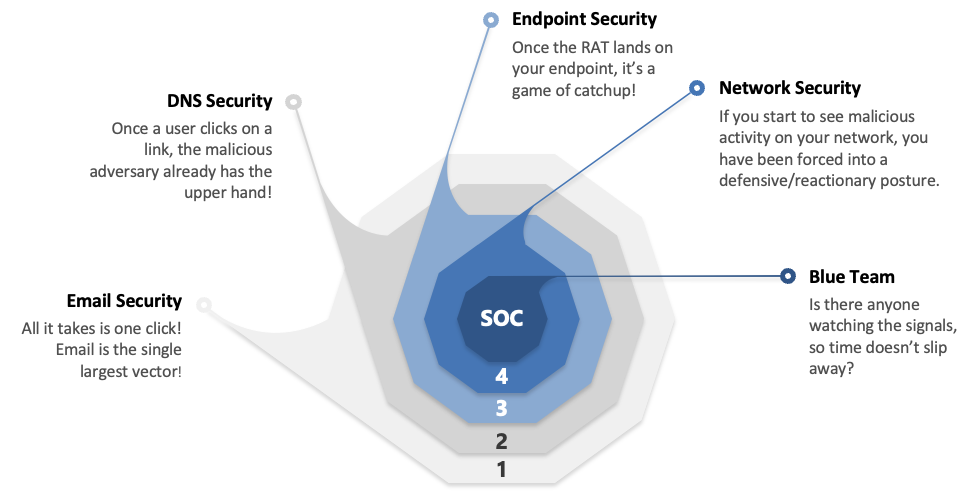
The most critical aspect of cybersecurity is understanding there’s no one silver bullet. We wish there were an easy button, but there’s not. Consider the graphic below. You need to be aware of where your most likely attack vectors reside and have defenses and response mechanisms in place.
Each of these zones has different tools and methodologies, and they all need to work together. You need orchestration and singular visibility into all the information, or telemetry, the tools are gathering so you can quickly correlate and prioritize risk.
Let’s explore key categories that have emerged to address this.
What Is EDR?
As its name implies, Endpoint Detection and Response (EDR) focuses on protecting anything that connects to the internet (laptops, mobile devices, servers, etc). With the distributed nature of the way we do business, there’s a heightened focus on protecting the endpoint now that workers are no longer behind a corporate firewall.
Most EDR tools offer protections such as:
- Patching to fix any vulnerabilities that attackers might take advantage of.
- Admin rights management to ensure only authorized users can access certain endpoints.
- Attack blocking to protect endpoints from harmful behavior.
- Full category-based blocking to protect applications with similar features.
What Is XDR?
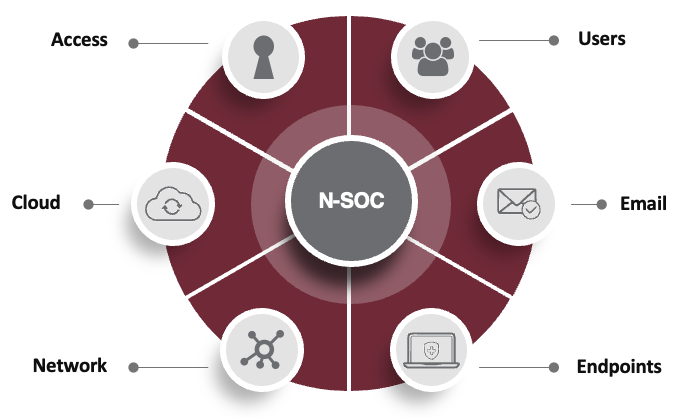
Extended Detection and Response (XDR) is a much more comprehensive approach. It protects all six threat vectors, not solely endpoints. This is a critical distinction because bad actors don’t just try to access your data through your teams’ devices. Your network, employees, access points, devices, cloud solutions, and email communications are all points of vulnerability.
XDR provides layered defenses for each of these vectors. Think of this method as protecting a castle from invaders. You want multiple layers—watchtowers, a moat, a high wall, archers, and a powerful army—to keep bad actors from entering and causing damage.
XDR delivers the most comprehensive threat protection and response and defends these entry points to help fend off cyberattacks such as:
- Customer Account Takeover
- Distributed Denial-of-Service (DDoS) Attacks
- Malware
- Phishing
- Ransomware
- Zero-Day Threats
What Tools Are Used in Cybersecurity?
The tools are constantly changing as technology and cyber threats evolve. Rather than investing time and money chasing individual tools that can quickly become outdated, businesses should focus on functionality first, and then see which cybersecurity software tools are best at the time to provide those functions.
What Tools Are Used in EDR?
To guard against endpoint threats, cybersecurity teams can use various EDR tools and techniques, including the following, just to name a few:
- Firewalls
- Next-gen Antivirus (NGAV)
- Endpoint Protection (EPP)
- Incident Response and Threat Hunting
- Security Operations Center (SOC)
What Tools Are Used in XDR?
XDR defends six common threat vectors. While including the full functionality of EDR, XDR extends to include the network, email, cloud, users, and access. XDR provides a single pane of glass for visibility and management across the enterprise and includes the following:
- XDR includes and extends beyond the EDR toolset
- DNS security
- Network analysis and visibility
- Advanced email protection including inbox security
- Cloud storage security
- Security Operations Center (SOC)
- Security Investigation and Event Management (SIEM)
While tools are important, true XDR adopts a function-first approach. Bad actors are constantly changing their tactics, and tool vendors are struggling to keep up. The best tool today may not be leading the pack tomorrow, so your defenses must be adaptable. The purpose is to maintain the highest level of protection as new threats and technologies emerge.
What Is the Most Important Tool in Cybersecurity?
The best tools for cybersecurity aren’t actually tools! It’s the mindset of having a layered defense across your entire enterprise—and then select the tools that help you achieve this. Technology quickly evolves, becomes obsolete, then innovates further, so it’s vital to constantly evaluate and update the tools you use to keep up (or get one step ahead) with the current cybersecurity landscape. That’s why it’s better to focus on your cybersecurity strategy first and then find tools to support it rather than trying to fit a strategy around your existing tools.
Stay Vigilant and Agile with DataEndure
You didn’t get into business to do this, but we did! As a managed security services provider with four decades of experience, you don’t have to go it alone.
With DataEndure as your partner, you can develop a mindset that’s equipped to handle today’s cyber threats with cutting-edge tools at your disposal. Here’s how we help your business protect against rapidly advancing cybersecurity challenges.
- Identify potential threats and weak points in your security system.
- Create a strategy to address those threats and weaknesses using XDR best practices.
- Implement the best tools and processes for your specific situation.
- Establish a 24×7 security operations center (SOC) team that knows how to best leverage security systems and tools to protect your business.
- Adjust strategies and tools as your situation and potential cyber threats change.
- Training on cybersecurity best practices for employees
Cyber attackers aren’t waiting to take action—neither should you. Schedule a meeting today.