Chief Marketing Officer
Looking for a threat detection and response solution for your company often feels like drinking out of a fire hose. There are so many threat detection and response tools out there, and you may have no idea where to begin, especially given the bleak fact that 64% of businesses have experienced a cyber attack, and 50% will experience another one. You’ve got to arm yourself for the cyber battle.
Often people focus on choosing a cybersecurity tool, like those that protect endpoints. It’s easy to overlook a simple fact: tools don’t win a war. Tools without a strategy and human expertise are just tools. Effective threat detection and response requires a comprehensive, multi-layered plan, and a flexible, adaptive mindset that can evolve as your adversaries launch new techniques and tactics.
Essentially, endpoint detection and response (EDR) shouldn’t be the only strategy you employ, but rather one component of a broad defense system. To help you understand the cybersecurity landscape, we’ve put together this blog that highlights EDR tools and provides insight into how they fit into your overall security strategy.
What Are EDR Tools?
EDR (endpoint detection and response) tools provide advanced threat detection, investigation and response capabilities to protect your endpoints: any laptop, computer, phone, server, or other device that connects to your network. Most EDR tools offer protections such as:
- Patching to fix any vulnerabilities that attackers might take advantage of.
- Admin rights management to ensure only authorized users can access certain endpoints.
- Attack blocking to protect endpoints from harmful behavior.
- Full category-based blocking to protect applications with similar features.
With the distributed nature of work and data, protecting your endpoints is critical. Naturally, the question becomes: what are the best EDR tools?
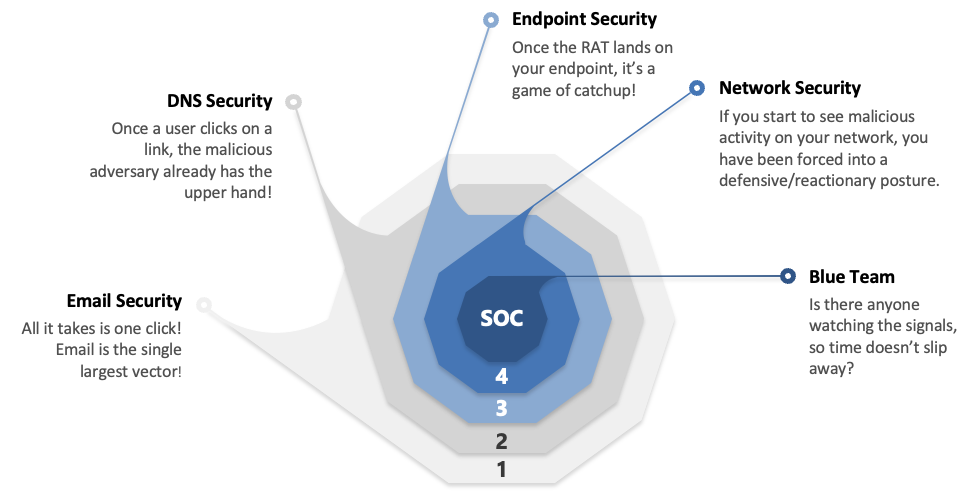
Today’s endpoint defense isn’t found in a single tool but requires a layered solution that delivers comprehensive visibility across all endpoints with advanced threat detection, investigation, and response capabilities. Security teams need to be fast to detect, fast to respond, and fast to remediate. To accomplish this, incident data search and investigation, alert triage, suspicious activity validation, threat hunting, malicious activity detection, and containment must be part of the solution.
That said, there are many other threat vectors to protect as well. EDR solutions can’t be your single line of defense against threats. Why? Because 80% of all malware comes from command and control procedures, not an endpoint.
Other common threat vectors include:
What Is the Downside of EDR Tools?
It’s not that there’s a downside to EDR tools, it’s that EDR by itself is incomplete. For example, here are three misconceptions about what EDR is and is not.
- Thinking EDR is a silver bullet. While having EDR security is important, using that as your only line of cyber defense leaves your business vulnerable. Without a layered solution you’re putting stressors on your EDR tool that it wasn’t designed to handle. If EDR is your one and only layer of defense, the burden is on your employees to adequately protect the endpoint, and that’s a risky gamble.
- Misinterpreting antivirus as EDR. Antivirus vendors have tried to morph into the EDR space. But is antivirus an EDR tool? Well, no. But the antivirus capability should be included in any EDR solution. The haphazard method of tacking on a few features to an antivirus solution doesn’t work against modern threats. Cyber environments—and their threats—are constantly advancing. Why would you resort to using 20-year-old technology to protect your systems? It’s like bringing a knife to a gunfight.
- A gap in human intelligence. Defending against today’s adversaries requires a 24x7x365 security operations center (SOC) staffed by experts. Without it, an EDR solution is incomplete, and you’re not poised to strike fast and eliminate threats.
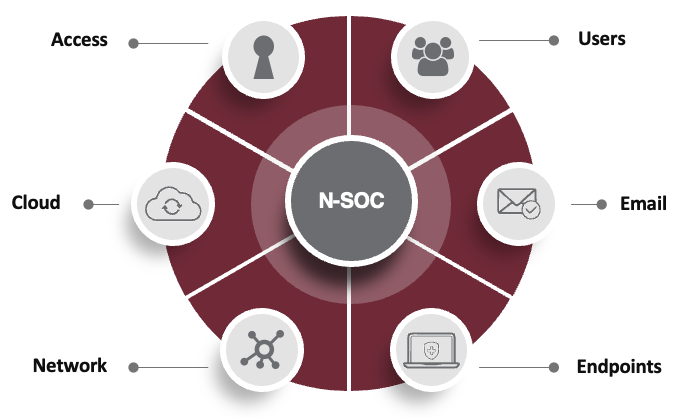
What Is XDR?
Extended Detection and Response (XDR) solutions need to go beyond the endpoints, extending protection to all threat vectors. XDR gives you the power to play both offense and defense against cyber attacks. XDR:
- Creates layers of defense so that fewer attackers reach your endpoints.
- Provides singular visibility across your environment to reveal vulnerabilities so you can fix them.
- Offers critical human intelligence to investigate, correlate, and remediate active threats.
- Protects your environment in ways that, frankly, many cybersecurity companies don’t pay attention to.
The concept of XDR is having an “X” that is dynamic. As threats adapt and tools change, the solution must have the flexibility to reinforce and bolster protection for each vector.
There are 5 critical areas that XDR should encompass:
When choosing an XDR provider, be wary of solutions that say they offer all-in-one XDR. Threat detection and response is a strategy, not just a plethora of tools. What’s more, watch for vendors tacking new features onto old products. Advanced technology needs advanced protections.
Go Beyond the Endpoints. Go With DataEndure.
When an adversary is in your environment, every minute counts. That’s why everything we do is laser-focused on eliminating dwell time. We go on offense to bolster your defense, delivering multiple layers of security, incorporating human intelligence, and extending beyond the endpoint. With this innovative approach and 4 decades of experience, DataEndure’s managed security solutions stand alone. We’ll:
- Cut nefarious dwell time to minutes, not months.
- Accelerate your security maturity within 30-90 days (we guarantee it)
- Reduce your cost by 50% vs building on your own
Ready to talk? Schedule a meeting to get started. You can also try out one of our free health checks to discover where you might have vulnerabilities in your systems.