AI is evolving—fast. Generative AI has already reshaped industries, helping businesses write, design, and code faster. But Agentic AI is taking things further. Instead of just assisting, it’s deciding, acting, and automating workflows—without waiting for human input. We’re moving from prompts to power moves—AI that doesn’t just respond but takes action. And it’s not just hype: Gartner named Agentic AI the top strategic technology trend for 2025, predicting it will autonomously… Read More
The AI Gold Rush: Why On-Prem AI is a Smart Bet
AI is revolutionizing industries at an unprecedented pace. From predictive analytics to real-time automation, businesses are racing to integrate AI into their operations. But as AI adoption skyrockets, a crucial question emerges: Where should AI workloads live? For years, the cloud has been the default answer. But now, a growing number of organizations are rethinking that strategy. On-premises AI is making a comeback—offering a powerful mix of security, performance, and… Read More
Seeing the Bigger Picture: Achieving Digital Resilience
When customers come to us, they often have a specific challenge on their minds: “How do I protect my network?” “Is my cloud environment secure?” “How can I lower my storage costs?” These are critical questions, but they’re often just one piece of a much larger puzzle. At DataEndure, we understand that the universe of IT and cybersecurity is far bigger than any single issue. Every aspect of your digital… Read More
Why Digital Resilience Demands a Unified Approach
When DataEndure marked its 40th anniversary, our CEO Kurt Klein reflected on how our mission has evolved: “If you look at us 40 years ago, we were all about resilience and data protection. That’s still true today, but the demands have become more complex and multifaceted.” Today, digital resilience isn’t just an advantage—it’s a necessity. Resilience means having the ability to adapt, recover, and thrive amidst ongoing technological, operational, and… Read More
DataEndure at 40: From Data Protection to Digital Transformation
As DataEndure marks its 40th anniversary, CEO Kurt Klein reflects on the company’s journey and what has fueled its longevity. DataEndure’s journey from a small value-added reseller to a leading technology integrator and managed security services provider reflects not only its resilience but its remarkable ability to adapt and evolve. With CEO Kurt Klein at the helm for nearly three decades, DataEndure’s story is a testament to innovation, strong partnerships,… Read More
Why Traditional Backups Fail Against Ransomware—and What to Do Instead
As cyberattacks grow more advanced, achieving digital resilience requires more than a traditional ‘set-it-and-forget-it’ backup approach. Legacy methods no longer provide the protection necessary against today’s sophisticated threats—especially ransomware. To safeguard your data and ensure business continuity, you need a modern backup strategy that encompasses cyber resilience as an integral part of a holistic approach, ensuring your systems can withstand and recover from attacks. The Limitations of Traditional Backups Traditional… Read More
Strategies to Operationalize Cybersecurity for Enhanced Data Protection
Organizations are navigating a perfect storm in data protection, driven by a rapidly evolving threat landscape and the exponential growth of data. With global data volumes projected to reach 175 zetabytes by 2025, the need for robust cybersecurity measures to protect that data has never been more critical. Operationalizing security measures is essential to effectively safeguard any organization’s vast amount of sensitive information. 8 Strategies to Operationalize Data Protection Operationalizing… Read More
Manual Selection vs. VMware Intelligent Policy?
Originally posted by DataEndure Principal Engineer, Brian Herbeck, on linkedin.com As enterprise environments grow, complexity follows. Many IT departments struggle to adhere to standard processes, maintain documentation and manage change. And significant gaps or changes can lead to backup failures. Current NetBackup versions allow for significant customization and control surrounding virtual machine protection. This article covers the advantages and use cases for using both manual selection and VMware Intelligent Policy…. Read More
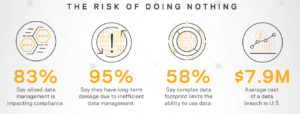
Your Unstructured Data is Holding You Back
You hear the term “unstructured data” often – data that is unorganized or doesn’t follow a structured data model. Gartner’s IT Glossary defines the term as “information assets organizations collect, process and store during regular business activities, but generally fail to use for other purposes.” Unstructured data is often blamed as the reason why traditional relational databases don’t meet the needs of Big Data. But that conversation doesn’t adequately describe… Read More
Case Study: DataEndure and Actifio Deliver Digital Resilience
This case study from Actifio on DataEndure is available in its entirety as a PDF here. Legacy Approaches Transformed with Modern Solutions DataEndure helps organizations protect, secure, access and capitalize on their data. However, they were seeing customers struggle with legacy systems and outdated strategies that no longer served business requirements. Customers needed a fresh approach that would take advantage of more advanced technology to accelerate, simplify, and reduce costs, especially… Read More