When customers come to us, they often have a specific challenge on their minds: “How do I protect my network?” “Is my cloud environment secure?” “How can I lower my storage costs?” These are critical questions, but they’re often just one piece of a much larger puzzle. At DataEndure, we understand that the universe of IT and cybersecurity is far bigger than any single issue. Every aspect of your digital… Read More
Why Network Security Must Be Your First Priority
For decades, businesses treated their networks like plumbing—an invisible utility that simply worked, delivering data from point A to point B. But today’s reality is far more complex. Your network isn’t just infrastructure; it’s the backbone of your organization’s security. If you’re still relying on legacy designs, you’re leaving yourself vulnerable in a world where threats evolve faster than ever. Today, the network and threats have changed, and your thinking… Read More
Why Digital Resilience Demands a Unified Approach
When DataEndure marked its 40th anniversary, our CEO Kurt Klein reflected on how our mission has evolved: “If you look at us 40 years ago, we were all about resilience and data protection. That’s still true today, but the demands have become more complex and multifaceted.” Today, digital resilience isn’t just an advantage—it’s a necessity. Resilience means having the ability to adapt, recover, and thrive amidst ongoing technological, operational, and… Read More
DataEndure at 40: From Data Protection to Digital Transformation
As DataEndure marks its 40th anniversary, CEO Kurt Klein reflects on the company’s journey and what has fueled its longevity. DataEndure’s journey from a small value-added reseller to a leading technology integrator and managed security services provider reflects not only its resilience but its remarkable ability to adapt and evolve. With CEO Kurt Klein at the helm for nearly three decades, DataEndure’s story is a testament to innovation, strong partnerships,… Read More
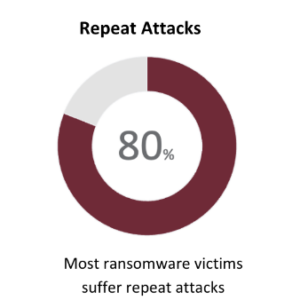
Why 80% of Ransomware Victims Suffer Repeat Attacks
In the realm of cybersecurity, the adage “lightning never strikes the same place twice” doesn’t apply. Organizations that have suffered one cyberattack are commonly targeted again, regardless of company size or industry. Ransomware by the Numbers Why Do Attackers Repeatedly Target the Same Company? The first cyberattack yields detailed insights into a company’s security architecture and response protocols. This intel becomes invaluable for orchestrating subsequent attacks that are often more… Read More
Securing the Future: How Network Resilience and Cybersecurity Interlock in the Digital Age
In the rapidly evolving digital landscape, the once-clear boundaries between network resilience and cybersecurity are increasingly blurred. These two critical areas have become interdependent, each reinforcing the other to create a robust defense against the myriad of threats targeting modern businesses. A solid security stance in today’s digital age demands a holistic approach, recognizing how network resilience and cybersecurity not only coexist but support and enhance one another. This synergy… Read More
Cyber Attacks Continue Long After They Fade from Headlines
When cybercriminals exploit a new vulnerability and attack a big brand company, it dominates news headlines. Yet, the reality is that adversaries persist in the shadows, long after initial reports fade from public view. Take the mass-exploitation of the MOVEit Transfer vulnerability, as just one example. In late May 2023, Progress Software first disclosed a zero-day vulnerability in their managed file transfer solution. The Clop ransomware gang leveraged the vulnerability… Read More
What does “Good” Cybersecurity Look Like?
In today’s threat landscape, it’s not a matter of if, but when a cyberattack will happen. How you respond to that attack is what truly matters. For this reason, cybersecurity efforts around threat detection and response are a top priority whether you’re a household brand or an up-and-coming business. But where do you start? What cybersecurity threats and solutions should you consider? How do you prioritize your cybersecurity efforts? To… Read More
ChatGPT is an infant that’s been given the internet
The “godfather of AI” just quit Google so he could speak freely about the dangers of generative AI products. The concern is the speed and acceleration without guardrails. Historically, we’ve had some really smart people in the hacker space that were doing things on the dark side. But now, we’ve just enabled many other bad actors who aren’t as savvy to do nefarious things. Zero Trust is 30 years old…. Read More
No easy button for cybersecurity
There is no “easy button” when it comes to protecting your data. While an endpoint-focused security solution is critical to protect the individual devices in your environment, such as computers, mobile phones, and tablets – it’s a very limited tactic. Combatting today’s threat actors requires a distributed defense in depth approach, not just a distributed endpoint security solution. As you assess your security tools – make sure you know what… Read More