While you and your team are out of the office enjoying downtime, this is when hackers get to work. Adversaries intentionally pick times when it’s difficult for your team to respond—such as evenings, holidays, and weekends. Take, for instance, car dealership SaaS platform CDK Global. They experienced a breach during the Juneteenth holiday, and then suffered another breach as they were starting to restore their systems. As of this writing,… Read More
Strategies to Operationalize Cybersecurity for Enhanced Data Protection
Organizations are navigating a perfect storm in data protection, driven by a rapidly evolving threat landscape and the exponential growth of data. With global data volumes projected to reach 175 zetabytes by 2025, the need for robust cybersecurity measures to protect that data has never been more critical. Operationalizing security measures is essential to effectively safeguard any organization’s vast amount of sensitive information. 8 Strategies to Operationalize Data Protection Operationalizing… Read More
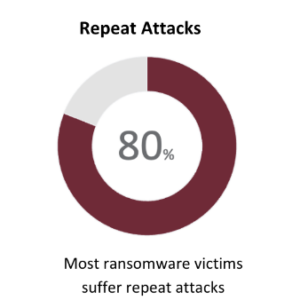
Why 80% of Ransomware Victims Suffer Repeat Attacks
In the realm of cybersecurity, the adage “lightning never strikes the same place twice” doesn’t apply. Organizations that have suffered one cyberattack are commonly targeted again, regardless of company size or industry. Ransomware by the Numbers Why Do Attackers Repeatedly Target the Same Company? The first cyberattack yields detailed insights into a company’s security architecture and response protocols. This intel becomes invaluable for orchestrating subsequent attacks that are often more… Read More
The New Frontier in Cybersecurity: A Swift Threat Response
Today’s digital age is a lot like the wild west. Cyber threats are like those old-time outlaws, always looking for a way to sneak into your operations. And just like in those classic westerns, it’s not enough to know there’s a bandit around; you’ve got to be quick on the draw to respond. That’s where we see a lot of businesses facing a real challenge. The Wild West of Cyber… Read More
Who Shares the Responsibility for Cloud Security?
Being in the cloud doesn’t mean your organization is secure. Maintaining proactive threat detection and response in the cloud is a constant, proactive process. What is meant by cloud security? While a cloud provider is responsible for securing their underlying infrastructure (physical, network, and host security), as an organization and user, you are responsible for securing your applications, data, user access, and configurations within your cloud environment. Mitigating cyber-risk requires… Read More
Securing the Future: How Network Resilience and Cybersecurity Interlock in the Digital Age
In the rapidly evolving digital landscape, the once-clear boundaries between network resilience and cybersecurity are increasingly blurred. These two critical areas have become interdependent, each reinforcing the other to create a robust defense against the myriad of threats targeting modern businesses. A solid security stance in today’s digital age demands a holistic approach, recognizing how network resilience and cybersecurity not only coexist but support and enhance one another. This synergy… Read More
Quantum Computing: The Next Frontier in Cybersecurity
A year ago, generative AI caught most businesses and governments by surprise. And while individuals, organizations, industry and regulators are only starting to scratch the surface discovering the opportunities and risks this new technology introduces—the next disruptor, quantum computing, is already knocking at the door. In fact, during the recent 2024 World Economic Forum Annual Meeting, IBM warned that quantum computing will wreak havoc on cybersecurity by the end of… Read More
Cyber Attacks Continue Long After They Fade from Headlines
When cybercriminals exploit a new vulnerability and attack a big brand company, it dominates news headlines. Yet, the reality is that adversaries persist in the shadows, long after initial reports fade from public view. Take the mass-exploitation of the MOVEit Transfer vulnerability, as just one example. In late May 2023, Progress Software first disclosed a zero-day vulnerability in their managed file transfer solution. The Clop ransomware gang leveraged the vulnerability… Read More
Embracing “Shift Left” in Cybersecurity
The concept of “shift left” has DevOps origins, and it’s about fostering a culture of responsibility. The aim is to detect issues earlier in a process or cycle, with an awareness that development choices impact the security of an application, its users, and the organization. From a security standpoint, this means integrating security measures at the beginning of the development cycle, rather than as an add-on after completion. Shifting Security… Read More
Cybercriminals Don’t Discriminate Based on Company Size
Last year, a staggering 76% of organizations were targeted by ransomware attacks. Out of those, 64% fell victim to the attack, and only 50% managed to retrieve their data after paying the ransom. Bad Actors Don’t Care What Size You Are While many small and mid-size businesses assume they’re too small to be in the crosshairs, this isn’t the case. Cybercriminals are opportunistic and are always on the lookout for… Read More
- « Previous Page
- 1
- 2
- 3
- 4
- …
- 10
- Next Page »