The reality of cybercrime in 2023 is that it’s a matter of when, not if, companies will face a cyberattack. It’s predicted that by 2025 cybercrime will cost the global economy $10.5 trillion. To put that in context, if you measured cybercrime against global economies, it would fall third (after the USA and China)!
To bring it even closer to home, 51% of organizations experience a ransomware attack; and 80% of those attacked experience repeat attacks. If it’s not you, it’s the business next door! This is why threat detection and response must be an integral part of every business’s operations.
A big part of the problem for many companies and employees is that they want (and need) to do cybersecurity well, but given the complexity and pace of change, simply don’t know where to start or don’t have the resources to fully address their needs.
This can lead to a mindset where businesses apply minor changes and precautions hoping for the best. This makes sense, as companies want to “check the box” and complete the “easy” tasks while letting more complex cyber protection measures fall by the wayside.
Therein lies the problem. Cyber threats are evolving fast, and the tools are struggling to keep up. Frankly, “set it and forget it” doesn’t cut it.
A solid security stance is about first developing the right mindset. That’s why we’ve put together this guide. Because the market is crowded and confusing, we want to highlight key concepts and considerations to guide your cybersecurity strategy.
You’ll learn the answers to questions like:
- What are the different types of security threats to organizations?
- What are the solutions to cybersecurity threats? Why is endpoint management not enough?
- What is a threat in network security? What about cloud storage and endpoint security?
- What is the future of cybersecurity? (Hint: it’s XDR!)
- How to monitor, manage, upgrade, and fine-tune your cybersecurity measures on an ongoing basis.
What Are the 6 Types of Cybersecurity Threats?
There are varied ways cyberattacks can be carried out, and they keep evolving as bad actors continue to advance their tactics. However, there are some broad categories that are worth exploring in more detail.
What Are the Six (6) Categories of Threats to Security?
Broadly speaking, the most common cyber attacks organizations experience are:
- Customer Account Takeover: A bad actor breaks into a customer’s account to access sensitive information like credit card or financial details.
- Distributed Denial-of-Service: Hackers overload your systems by sending false traffic to it, stopping systems from operating.
- Malware: Infected software infiltrates an entire business network or some portion of its devices, disrupting or halting work and stealing information.
- Phishing: Cybercriminals are expert social engineers, and are adept at tricking users into giving up sensitive information via fraudulent emails or websites, many of which are onramps for malware to be downloaded and execute.
- Ransomware: A version of malware that shuts down compromised networks or devices until a ransom is paid, and even then, may not restore service or returns data encrypted and unusable.
- Zero-Day Threats: These can be some of the biggest cyber security threats because they are brand new (and therefore unknown), so your security team – and many security vendors – have “zero days” to prepare and protect the IT environment.
What Are the Five 5 Types of Attacks on Network Security?
Network security threats and vulnerabilities are frequently overlooked. The traditional thinking when it comes to the network is, “if it ain’t broke, don’t fix it.” When asked how their networks might be improved to accommodate application flow, better security, and user experience, most still believe that what they have is adequate. There’s a flaw in that logic, though. Ask yourself two key questions:
- “Does ‘adequate’ protect you from the latest security threats?” and
- “Does it account for the needs of the modern mobile/remote workforce?”
The fact is, if you haven’t updated your network architecture in more than two years, you’re likely at risk.
With the move to remote work and distributed everything, businesses are finding their boundary devices overloaded and inadequate for the security challenges that come with a remote workforce. And their applications are similarly unprepared for this shift. Instead of being centralized, the network is now dispersed, with no defined edge. IT staff must shift their thinking from “we trust everything connected to the network” to “we don’t trust anything connecting to the network, regardless of location.”
For bad actors today, penetrating the network is the holy grail because, once they’re in, they have access to everything else. They look for weak points in the network, so they can steal data, damage the tech environment, or encrypt vital business applications and assets. By becoming more aware of the types of network threats and attacks, a company can learn how to prevent network attacks most effectively.
The 5 network security threats that are most common today are:
1. SQL Injection
The most common method used for SQL injection attacks is inserting malicious code through unmoderated data input sources. Once a network is infected in this way, the code can allow access to sensitive data or alter data to make it inaccurate.
2. Unauthorized Access
This attack is when a bad actor enters the network without permission. This can happen through weak password protections, networks that lack encryption, VPN access, or unattended, unprotected, or stale accounts and devices with high levels of access enabled.
3. Privilege Escalation
Once a hacker has entered a network, they’re now in the house! With this, their ability to do damage grows exponentially. They’re able to gain more access, allowing them to move across the network and identify sensitive information. This can happen in two ways:
- Horizontal escalation, where they access network elements adjacent to their entry point.
- Vertical escalation, where this hacker gets access to a higher level of privilege within the original network.
4. Adversary-in-the-Middle Attacks (AitM)
AitM network attacks happen when a hacker intercepts traffic as it travels between endpoints and the traffic destination. This can happen with both ingress and egress traffic from the network. This allows them to access and alter data and transactions in real-time.
5. Insider Threats
As painful as it is to consider, malicious staff who already have access to a network and confidential data can be a real threat to network security. Not having a way to monitor and/or detect internal threats is a common security blind spot in the network. Analyzing network user behavior to look for anomalies is often the only way to detect this threat.
What Is the Best Solution to Improve Security?
The best solution to combat cybersecurity threats is a multi-layered approach. One that protects each threat vector but also works in concert to deliver a robust security solution. Too many security tools and solutions focus on just one element of security, like endpoint protection.
The logic goes that if all the endpoints are covered, then no unauthorized users can gain entrance. With hybrid and remote workers using multiple devices to access different networks and clouds, it is naive to think an endpoint solution is enough. There are just too many possible points of entry, so if you have not protected your information assets more broadly you have no other lines of defense.
What Is the First Step in Protecting Against Security Threats?
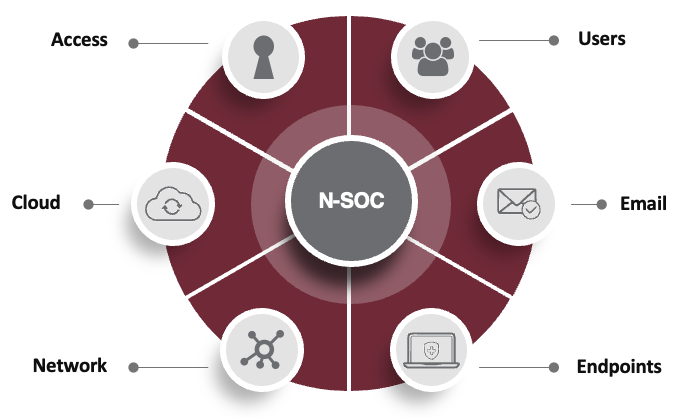
The first step a company needs to take in their security maturity journey is to determine what you need to protect. It’s important to understand the different threat vectors, the places where bad actors can break in and cause havoc. Common threat vectors include:
Once a business has a clear idea of what you need to protect, it’s time to think about the why—for each vector, why is it important to provide comprehensive protection? For example, think about where your users are, how they are accessing data, and what regulatory requirements you need to meet.
Next, get a clear understanding of your gaps. What you don’t know can take down your business. Conducting a security controls assessment and vulnerability assessment is an important part of gathering this insight and getting the full picture.
Finally, it’s vital that your company has an advanced threat detection and response strategy that covers every threat vector. You need to think in terms of layers of security and defenses to protect your company, and not get stuck in that “buy one tool, set-it-and-forget-it” mode. Cybercriminals are constantly evolving their approach, so you need a dynamic security strategy that keeps pace.
What Are Five Methods to Detect and Prevent Cybersecurity Threats?
There are a variety of solutions available for cybersecurity within an organization. The five main methods are:
1. Endpoint Detection and Response (EDR) – EDR monitors and protects endpoints, which include any devices that connect to a network. EDR evolved from antivirus tools, and is basically an antivirus solution with an expanded set of security features. It focuses not only on changed files, but on detecting nefarious behavior. However, because it only protects endpoints, EDR, by definition, leaves other threat vectors unprotected.
2. Managed Detection and Response (MDR) – For organizations that want broader coverage for more threat vectors, but don’t have the internal IT team or budget to handle themselves, MDR is a great option. A true MDR will cover more threat vectors, and include both network and endpoint protection, a 24/7 staffed security operations center (SOC), continuous vulnerability assessment, and controls validation.
3. Security Information and Event Management (SIEM) – Security tools are only as good as your ability to quickly make sense of the information they are giving you and act on it. Essentially, a SIEM is the bridge between the massive amount of information and the experts who need to correlate the data (to determine what’s a threat and what’s not). SIEM helps support threat detection, compliance, and security incident management by providing the information needed to spot abnormal behavior.
Unfortunately, the SIEM is often used only as a forensics tool after an attack, rather than a powerful, proactive indicator of threat or compromise. To be able to use it offensively, you need a security operations center (SOC) with 24/7 staffing and expertise to understand and correlate the data correctly. Many organizations can’t or won’t make this investment, and the adversaries know it.
When a SIEM works as intended, an organization that generates several billion alerts a year can winnow that down to 100 alerts that need action. Every security tool you add increases the number of alerts you get exponentially, and alerts in the number of billions is average for a mid-size company.
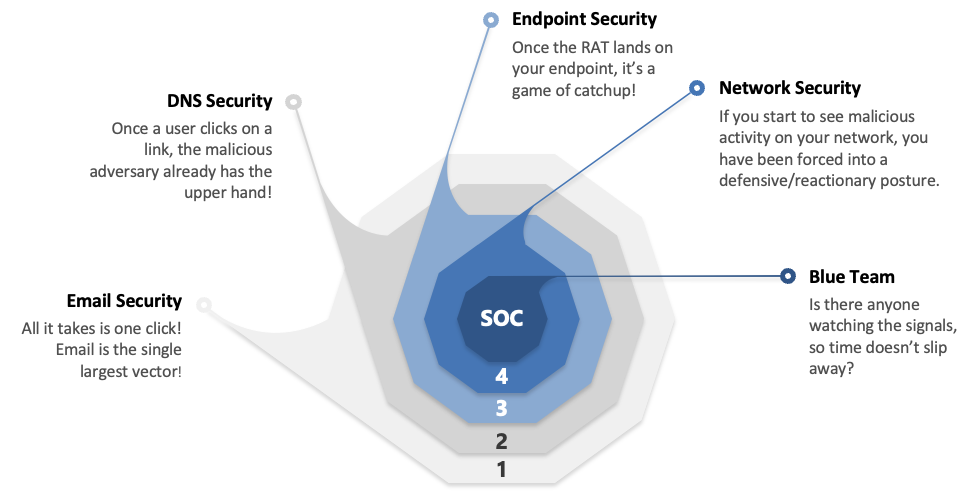
4. Network Detection and Response (NDR) – In today’s connected age, networks play the leading role–yet are often overlooked from a security perspective. The industry is hyper-focused on protecting the endpoints; however, this does not stop hackers from being able to access the network. Alarmingly, the average hacker infiltrates a network and stays there for six months before they are discovered known as dwell time.
When NDR is done right, it cuts dwell time down to moments, or even seconds. NDR puts a magnifying glass on your entire network to allow you to see where most traffic is happening, what devices connect to it, and where slowdowns may be occurring.
Core to NDR is the concept of Zero Trust Network Access (ZTNA) where devices connected to your network have to prove that they can be trusted. If that device doesn’t meet the requirements for where, what, or when the network is being accessed, then they’re denied access.
5. Extended Detection and Response (XDR) – XDR provides the most expansive protection for an organization and includes all the threat vectors, from clouds to networks to endpoints and beyond. It’s a layered approach, with different levels of security all working together to eliminate gaps and holes where cyber criminals can sneak in.
A layered defense strategy is designed with one purpose–to dramatically reduce dwell time:
- Reduce the load on the endpoint in three of the five layers
- Increase the amount of telemetry to accelerate detection and remediation
- Fortify email security because it’s where 93% of where attacks begin
- Deny access to bad sites and links with DNS protection
- Enhance visibility across the enterprise with expert eyes on glass for monitoring, escalation, and remediation.
DataEndure: The Cybersecurity Solutions Company You Need
Maintaining a solid cybersecurity posture is a challenge for most companies, that’s why DataEndure offers a suite of managed security solutions to make it easy and affordable. Here are some of the biggest reasons businesses reach out for assistance, and what we can do to help.
A Data Breach Occurred
When your business assets have been compromised, time is of the essence. You need real solutions, right away. DataEndure has four decades of experience helping companies in your position:
Identify the breach source Isolate affected systems Remediate and restore business operations Evaluate the overall security controls in place Improve protection and detection going forward
Compliance and Cyber Insurance Requirements
Many industries have specific requirements a business must meet or face severe penalties. But navigating the constantly evolving regulations and updating your security posture to meet them can easily put you over budget and out of time. DataEndure stays up to date on compliance requirements, so we can help you understand if your existing controls are enough; or how and where you need to adapt. We’ll also provide recommendations on long term solutions to help keep you compliant even as the rules change.
In addition to compliance, many organizations are looking to reduce their financial risk through cyber insurance. With the continued rise of cyberattacks and skyrocketing costs, U.S. insurance entities have responded by becoming more selective about who and what gets covered. They raised premiums and minimum cybersecurity baseline requirements to a higher level of maturity seen historically in only regulated industries. With DataEndure, you’ll have a partner to help you achieve and stay qualified for cybersecurity insurance.
Security Posture Uncertainty
Cybersecurity can feel like a very scary place, especially if you’re in the dark about where you stand. That’s why DataEndure offers a complimentary security health check so you can shine a light on what things are working well and where your vulnerabilities are. The more you know, the better you are able to protect your assets.
Gap in Internal Skills
Finding staff with the right experience to navigate the increasingly complex world of cybersecurity can be a challenge. A huge number of companies do not have the employees, time, or training to be able to create and monitor security to the level it needs to be.
That’s where a full-service managed security service provider like DataEndure comes in. With a consumption model, the burden of researching the best tools, buying tools, staffing and maintenance is on the experts, helping companies accelerate and maintain their security maturity, often for significantly less cost.
DataEndure’s managed security services offer on-demand expertise, so your staff can focus on what they do best, and we can focus on:
- Monitoring the network and alerting you to potential threats, 24×7
- Assessing vulnerabilities
- Testing your security controls monthly with simulated attacks
- Elevating alerts that are high priority to avoid alert fatigue
- Providing the best tools and professionals to stay at the forefront of security
- Implementing rapidly, in 30-90 days
- Giving you the lowest cost and overhead expenditure possible
When you’re ready to make sure your company’s digital assets are protected, contact us to get started.