Did you know that it takes organizations an average of 277 days (or about nine months) to identify and contain a data breach?
These lengthy data breach lifecycles (known as dwell time) are associated with some serious implications—for example, a dwell time longer than 200 days costs about $4.86 million on average, whereas a data breach shorter than 200 days costs roughly $3.75 million (better—but still about $3.75 million than any organization wants to pay).
And it’s not just about the money! Data breaches and other cyber attacks often have disastrous consequences, like lost or leaked data, decreased company reputation, and even legal ramifications. With all of this in mind, it’s no surprise that 60% of small businesses fail after being hacked.
It’s not a stretch to say that the stakes couldn’t be higher.
Unfortunately, cybersecurity efforts around threat detection and response are complex and ever-changing, which makes keeping up with advanced threats and bad actors difficult.
It’s not as simple as employing antivirus software anymore. Even endpoint detection and response (EDR) tools are quickly becoming outdated, giving way to more comprehensive extended detection and response (XDR). But what exactly do all of these terms mean? And how do you find the right solution to improve your security posture?
To help you, we’ll explore questions like:
- What is EDR and why does it matter?
- What does an EDR system do?
- Are EDR products still relevant? Or is XDR the way of the future? (Hint: it’s XDR!)
What Is Endpoint Detection and Response?
Endpoint detection and response describes the strategy and technology that continuously observes the endpoints of a network in order to monitor, analyze, and respond to certain types of cyber attacks. What is considered an endpoint in EDR? Essentially, an endpoint is any physical device that connects to a network. Endpoints include everything from laptops and desktops to smartphones, servers, IoT (Internet of Things) devices, and virtual machines.
Because of the increasingly digital and distributed world we live in, these endpoints are necessary to power today’s businesses. Yet, unprotected and unmonitored endpoints can be extremely vulnerable to cyberattacks like ransomware and malware, which underscores the vital importance of being able to detect anomalies as quickly as possible. But does EDR go far enough? Spoiler alert, it doesn’t. After all, the endpoints aren’t the only entry points that cyber criminals target.
Think about today’s digital landscape. With the rise of remote work, your people (data, and devices) could be literally anywhere. And cyber adversaries are well-versed in the number of areas they can break in.
Today’s major threat vectors include:
So is protecting endpoints important? Absolutely. However, they are only part of the equation. Many organizations have built their security posture around this one threat vector while neglecting the others. That’d be like putting on a swimsuit and going out in a blizzard—you simply don’t have enough protection. Just like avoiding hypothermia, it’s all about layers. An EDR-only approach leaves businesses out in the cold.
What Are Endpoint Detection and Response Tools?
In theory, EDR enables businesses to monitor their endpoints and promptly respond to potential attacks. Of course, endpoint detection and response tools are not created equally and have varying capabilities. Some are true endpoint detection and response solutions, while others don’t offer much more than antivirus capabilities.
With that said, key features that define a true EDR solution include:
- Data collection: What data does endpoint detection and response collect? EDR tools gather and collect system- and user-level activities and events to offer security teams the data they need to identify anomalies and patterns. (Don’t have a security team? Don’t worry, DataEndure can help. More on this later!).
- Behavioral and signature analysis: a key differentiator between anti-virus software and EDR tools is the collection and analysis of behavior in addition to signature-based data. Signatures simply compare different code to find differences rather than looking at how users and devices are acting. Bad actors are intelligent enough to beat signature-based tools, which makes the behavioral data of EDR extremely valuable.
- Real-time detection and remediation of complex threats: effective EDR requires massive amounts of telemetry (think needle in a haystack), so EDR tools must be able to not only collect data but also provide threat intelligence capabilities to perform automated anomaly detection. This enables security teams to analyze and respond more quickly.
- Firewall control: for control of network connectivity to and from devices including location awareness. Firewalls are set up to provide a barrier between a company’s network and any external networks. They prevent unauthorized access while still allowing for legitimate authorized traffic. The challenge with firewalls is the edge has moved out in our distributed world, therefore the efficacy is more limited.
- Risk management: to continuously inspect your vulnerability and security controls, so you can inspect what you believe is working vs what is actually happening. The days of the annual penetration test are over–bad guys don’t hit you once a year. You need to be alerted of vulnerabilities on a moment by moment basis.
- Centralized and real-time visibility: Organizations are dealing with a massive amount of endpoints and data. Being able to monitor and correlate all of that telemetry in one place offers organizations a single source of truth, with visibility across all endpoints. This increases speed and efficiency, which is especially important for small or overburdened IT teams.
- 24 x 7 Security Operations Center (SOC): to get the full value of the solution, you need expert human eyes on glass.
What Is EDR Versus…
When we talk about endpoint detection and response, there are several terms that often get thrown into the discussion. Most notably, terms like “antivirus” and “extended detection and response” (XDR) are often used synonymously with EDR. Below, we explore what these terms mean, how they differ from one another, and which one truly provides comprehensive detection and response.
EDR vs Antivirus
Is EDR the same as antivirus software? No, it’s not. While there are some overlapping features of EDR and antivirus, cybercriminals are now savvy at evading AV detection. It’s using old technology to combat advanced threats.
Put simply, antivirus (AV) is responsive in nature; it kicks into gear after something is on a system. AV scans device files for viruses, and removes any infected files that are discovered. To accomplish this, most antivirus tools use signature-based scanning. Essentially, they compare code on a device to a known list of “bad” code to identify threats. While this can be effective against existing malware, it does mean that most AV tools are not equipped to detect new kinds of threats—such as zero-day threats—that aren’t yet on their list.
Additionally, bad actors know antivirus tools look for signatures, and they know how to fool the system—which is why behavior is the more important indicator of compromise than using signature-based scanning. User and device behavior is the most important data to collect and analyze in order to detect nefarious activity.
EDR, on the other hand, offers advanced protections compared to antivirus. EDR solutions grew from traditional antivirus tools to offer added features and functionality we discussed in the previous section, including telemetry, real-time monitoring, firewalls, whitelists, and a centralized dashboard. Basically, EDR solutions are more comprehensive than antivirus tools.
In short, if you’re wondering “do I need antivirus if I have EDR,” the answer is no. EDR solutions contain all the functionality of traditional antivirus tools and then some. If you simply have antivirus and are wondering if it is enough, the answer is “you are at risk.”
EDR vs XDR
Another common acronym you may hear when researching EDR solutions is XDR, or extended detection and response. If EDR evolved from antivirus tools, then XDR represents the third evolution of this type of solution and the cutting edge of cybersecurity. We like to say “it’s all about the ‘X’.” While “E” is limited to the endpoint; think of “X” as providing security across all identified threat vectors.
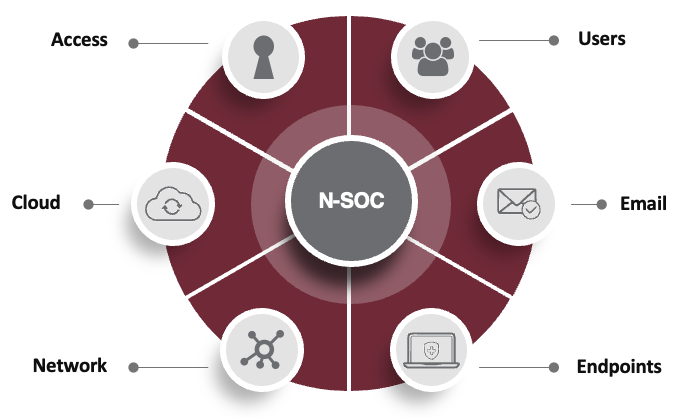
EDR, as we’ve discussed thus far, exclusively offers protection for an organization’s endpoints. However, these devices aren’t the only potential weak point in a company’s environment. As previously shown, endpoints are only 1 of 6 critical vectors that require protection. This is especially the case for companies operating under hybrid and remote models, where workers need secure access to cloud applications and data from anywhere. That’s where XDR comes into play.
So, what is the difference between EDR and XDR? It comes down to what you’re trying to protect. At a high level, XDR provides advanced security protection across all 6 threat vectors vs EDR’s one. This provides unified visibility across the threatscape. It simplifies and accelerates your ability to find and eradicate threats.
Is EDR Outdated?
While EDR is an important piece of the puzzle, it is not sufficient and outdated due to its limited coverage. While it served its purpose for years—and even inspired the creation of more advanced tools like XDR—it struggles to keep up with today’s pressing demands. Factors like remote and hybrid work, new and more sophisticated threats, new pressures on the network, significant cloud deployments and even alert fatigue call for a more comprehensive security solution.
In fact, even back in December 2021, Forrester was reporting that EDR is “mostly dead.” They argue that while EDR may still act as a stepping stone to better overall security posture, it’s no longer enough. To keep up with increasingly advanced cyber attacks, XDR technology has become the gold standard in this space. Yet, it’s important for businesses to proceed with caution when selecting an XDR solution. Not all XDR providers have the same approach.
You need a layered and comprehensive solution with an expert team that enables you to:
- Detect advanced threats across endpoints, cloud, network, or server environments, providing a more holistic view of an organization’s security posture.
- Track threats and correlate telemetry to accelerate response times.
- Get alerted solely on critical issues to decrease alert fatigue—something that 79% of IT professionals report as an issue.
- Consolidate, evaluate, and constantly improve the tech stack to stay up-to-date and ahead of evolving cyber criminal techniques.
- Perform continuous incident response (CIR)
- Reduce dwell time to minutes vs months
Just like EDR replaced traditional antivirus tools, XDR is today’s gold standard for defending your business.
DataEndure: Protect Your Business, Data, and Assets
Without an uncompromising security posture, organizations are vulnerable to the deluge of new cybercriminal tactics and advanced attacks coming at them. While cybersecurity is a foundational requirement, getting it right can pull focus from your core business strategy. At DataEndure, we have your back.
Our extended threat detection and response offerings allow you to simplify your tech stack, scale your services as needed, and quickly secure your business, data, and assets. Everything we do is about ensuring your business success–and it all comes down to timing. Our ability to eradicate bad actors before they can take you down is unprecedented.
While the industry average for nefarious dwell time is 6 months, we decrease dwell time to just 6 minutes!
Operating with a small or nonexistent security team? That’s ok! Our managed security services give you the advantage of security protection without the burden of finding, hiring, and onboarding a team of your own.
At DataEndure, we take your security—and your success—seriously. We offer complimentary health checks to help you understand where you are now and where there is opportunity to improve your security posture. Get started with one of our health checks or reach out to our team to learn more.