
Given the growing number of threat vectors, continuous vulnerability assessments play a critical part in keeping your sensitive data secure, helping to keep you one step ahead of attackers and new threats that emerge daily. If you know where the holes are, you can remediate them before the hackers find them.
Yet even savvy organizations struggle to keep up with the volume and prioritization of alerts from multiple tools and systems. To keep your data secure, you must continuously scan your systems and devices to detect vulnerabilities as they arise. Once detected, you must assess the potential threat of those vulnerabilities and prioritize your remediation activities to deal with the greatest threats first.
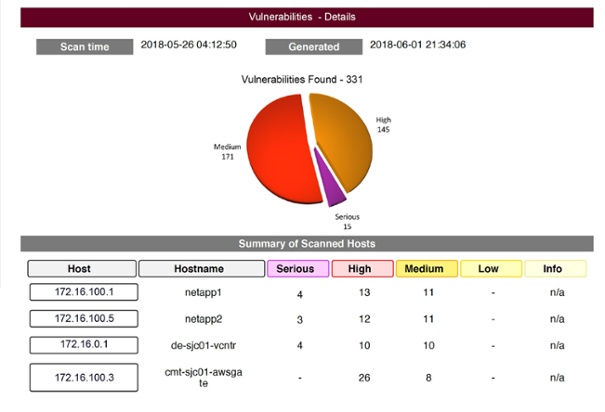
DataEndure’s Vulnerability Assessment is included in our SOC-as-a Service, and is a continuous service that helps you:
- Define: Log and categorize all related network-based assets discovered in the scan.
- Identify: Identification and detection of vulnerabilities across your network leveraging Common Vulnerabilities and Exposures (CVE) which are maintained by MITRE. Includes detailed information relating to configuration issues and missing security patches on network-based assets such as a firewalls, routers, web servers, application servers, etc.
- Classify: Assign severity scores to vulnerabilities using Common Vulnerability Scoring System (CVSS), the universal open and standardized method for rating IT vulnerabilities and determining the urgency of response. Scores range from 0 to 10, with 10 being the most severe. DataEndure leverages CVSS version 2 (CVSSv2) for scoring.
- Prioritize: Present comprehensive findings and analysis in a way where issues can be segmented by severity level, accompanied by information on recommended actions for remediation.